Protecting Critical National Infrastructure (CNI) through extended global visibility
Team Cymru offers a range of capabilities specifically tailored to protect Industrial Control Systems (ICS) and Operational Technology (OT), which over the years have been increasingly targeted by hostile nation-state threat actors as well as lesser skilled “hacktivist” groups.
Unlike standard IT environments, OT systems often utilize legacy protocols and have long equipment lifecycles, making proactive external visibility essential.
By focusing on the networking stages of the ICS version of the MITRE ATT&CK framework using Team Cymru’s visibility, specifically Reconnaissance and Command and Control, OT defenders can identify scanning and exploitation attempts against exposed infrastructure and track malicious infrastructure before attackers can establish persistence.
Cybersecurity industry experts continue to warn that critical national infrastructure (CNI) sector organizations need to enhance their visibility into their own remote facilities and technical OT system.
"Utilities need to treat external exposure and asset blind spots as intelligence problems, not just configuration issues. Energy-sector OT environments are becoming increasingly exposed as legacy systems connect to modern networks without corresponding gains in visibility or monitoring. What stands out in these findings is how quickly serious risks emerge once traffic is observed, suggesting attackers are likely identifying the same weaknesses just as fast. Closing these gaps requires continuous visibility into OT communications and the context to understand what ‘normal’ behavior actually looks like.” - Will Baxter, Field CISO at Team Cymru.
"The recent Poland attacks confirmed that the adversary doesn't just teleport to the perimeter; they 'commute' via Operational Relay Boxes (ORBs) to pre-position themselves months in advance. Tracking this external infrastructure allows defenders to spot the threat left of boom, burning the adversary's bridge before they can cross it to deliver kinetic effects. To survive a sophisticated campaign, we cannot operate with blind spots; we need external telemetry to track the adversary's intent and internal deep-packet inspection to catch their specific 'living off the land' tactics. External visibility tells you who is knocking at the gate, while internal visibility is the only way to see what physical process they are attempting to disrupt once inside and capturing transient data for root cause analysis afterwards." - Mark (Magpie) Graham of Dragos Inc.
Evolutions of the ICS and OT Threat Landscape in 2025
To help track the evolution of ICS/OT threats, Team Cymru researchers supported the development of the Cyber Incident Tracker for Electric Power Systems (CITEPS), a project created by Prof. Dr. Luiz F. Freitas-Gutierres.
The evolution of ICT/OT threats can be marked by two main eras. The first era involves adversaries experimenting with these sophisticated digital weapons. The second era can be marked by an increasing usage and adoption of these capabilities by adversaries, often attributed to nation-state intelligence services.
2010–2019: The Era of Experimentation
This period marked the introduction of specialized digital weapons targeting ICS, leading to a mix of espionage and destructive attacks. This includes the deployment of Stuxnet in 2010, which is noted as the world’s first publicly known digital weapon against ICS, physically destroying centrifuges at the Natanz nuclear facility in Iran. Subsequent malware became more specialized, such as Industroyer which was used in the 2016 Ukraine power grid attack to disrupt electricity, a critical event that signaled a shift toward direct grid manipulation. The ceiling was raised further in 2017 with Triton malware, which specifically targeted safety instrumented systems at a Saudi Arabian petrochemical plant, threatening physical safety mechanisms and threatening the lives of the workers there.
2020-2026: The Era of Adoption
This period was first marked by the attack on Colonial Pipeline (2021), which has been classified as critical in CITEPS because the ransomware attack forced a shutdown of the pipeline for days, affecting both IT and OT. In 2022, we observed the deployment of Industroyer2 ICS malware and CaddyWiper destructive attacks, which represented renewed attempts at taking down electrical substations in Ukraine. Also in 2022, new ICS tools like Pipedream, a multitool for attacking various OT devices, was uncovered alongside FrostyGoop in 2024, which was a malware specifically designed to attack Modbus TCP-enabled devices to disrupt heating systems.
Attack on the Polish Electric Grid
Crucially, the Computer Emergency Response Team of Poland (CERT-PL) identified a disturbing new ICS/OT campaign against Poland which it attributed to the Russian intelligence services. On December 29, 2025, a coordinated series of destructive cyberattacks struck Poland's energy infrastructure. The attacks targeted at least 30 wind and solar farms, a Combined Heat and Power (CHP) plant serving nearly 500,000 customers, and a private manufacturing company. In this campaign, the adversary reportedly severed communication between the renewable energy facilities in Poland and the Distribution System Operators (DSOs). While this effort did not stop electricity generation or destabilize the Polish grid, it removed remote control and visibility from the operators.
Plus, to further disrupt the IT environments, the adversary reportedly deployed a custom data-wiping malware dubbed DynoWiper by ESET. The tactics uncovered by ESET during the DynoWiper incident closely resemble those they saw previously involving another data wiper, dubbed ZOV, in Ukraine. Technical analysis of DynoWiper led ESET to assess with moderate confidence that it was developed by the Russia-aligned threat group Sandworm.
Threat Hunting for Adversary Activities
According to CERT-PL, in each affected facility, a FortiGate device was present, serving as both a VPN concentrator and a firewall. In every case, the VPN interface was exposed to the internet and allowed authentication to accounts defined in the configuration without multi‑factor authentication. From the indicators of compromise (IOCs) shared by CERT-PL, we can see in Team Cymru’s WHOIS data that two of the pairs of IPs were hosted on BlueVPS (AS62005) and Hostinger (AS47583).
Using Team Cymru Scout to query netflow communications, we can search for all BlueVPS and Hostinger IPs that have been communicating with Fortigate systems in Poland, using a search such as tag = "fortigate" cc = "PL" comms.asn = "62005,47583". Using queries like this to identify trends such as changes in an adversary’s behaviour activities can help better prepare your organisation for such threats.
ICS-Specific Exposure Management
Team Cymru’s data also allows defenders to discover internet-exposed ICS devices, such as PLCs, RTUs, and SCADA systems, before they are discovered by adversaries.
Manufacturer Pinpointing: Using ICS-specific tags in tools like Scout, organizations can identify at-risk assets by manufacturer or product family
Passive Monitoring: Netflow data provides passive visibility into OT environments, which is critical for remote facilities where active internal network scanning or agent-based scanning might be too disruptive.
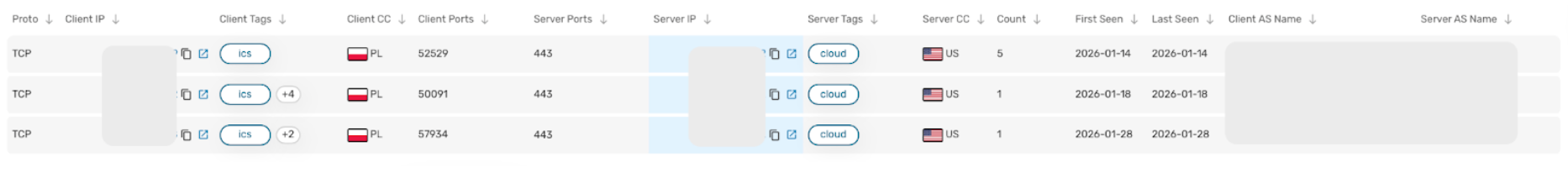
Team Cymru customers with Scout can track these activities using the following Scout query:
comms.tag1 = "ics" comms.tag2 = "scanner"
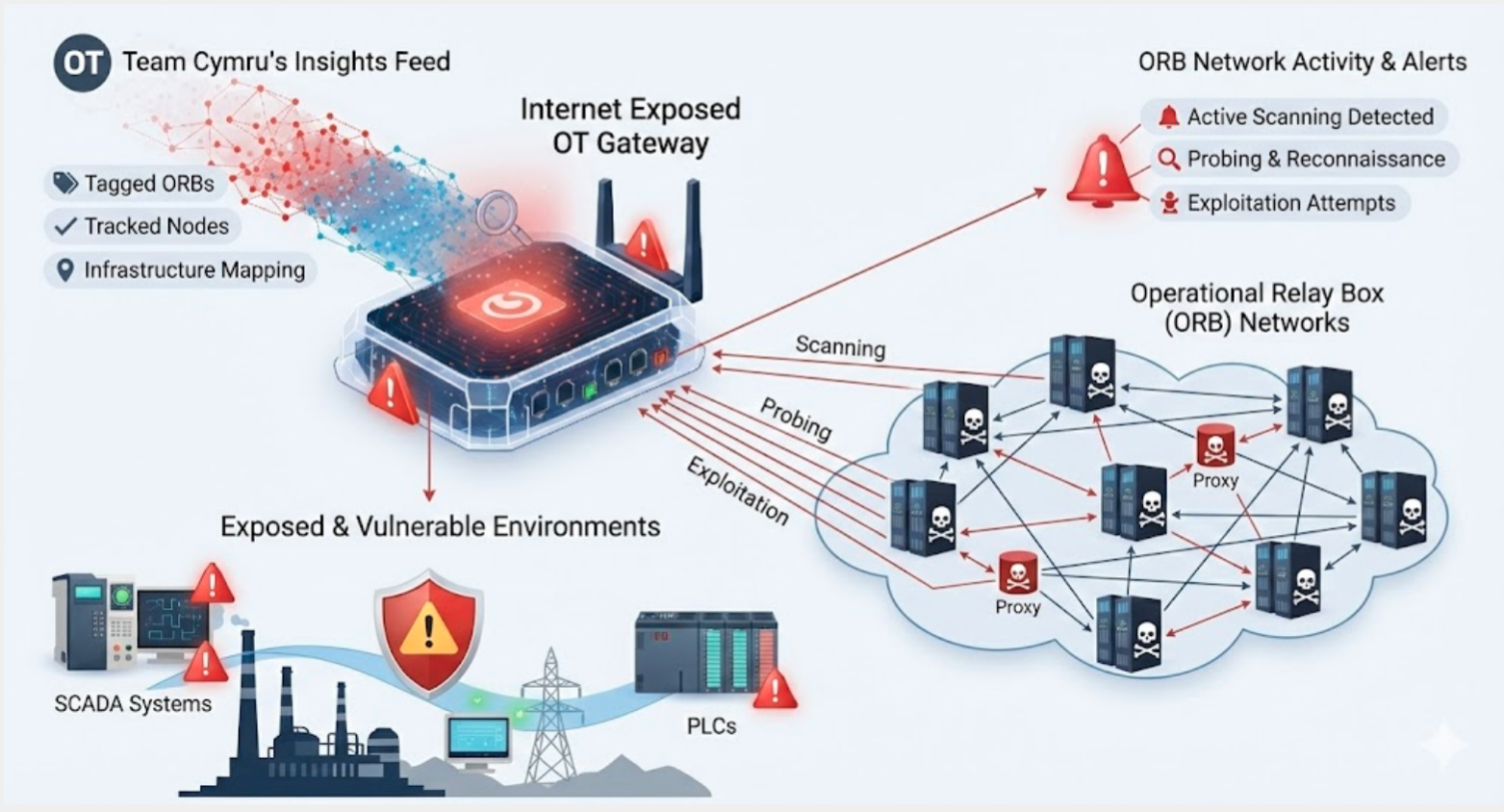
ORB Networks Targeting ICS/OT environments
Tracking specialised infrastructure is another key capability to defend against advanced hostile nation-state threats. Team Cymru supports these efforts by helping our customers specifically monitor Operational Relay Box (ORB) networks, often controlled by China-nexus adversaries, and other anonymization infrastructure that mask attacker origins when performing reconnaissance or exploitation against critical infrastructure.
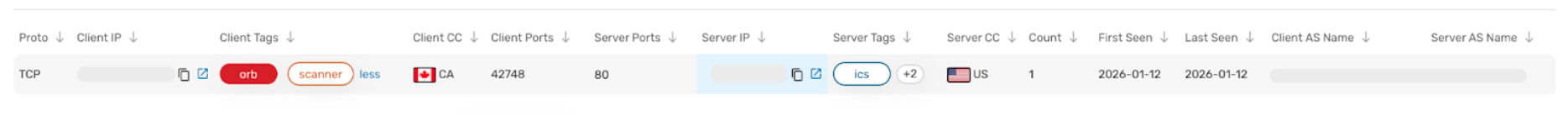
Team Cymru customers with Scout can track these activities using the following Scout query:
comms.tag1 = "ics" comms.tag2 = "orb"
Threat Feeds for ICS/OT environments
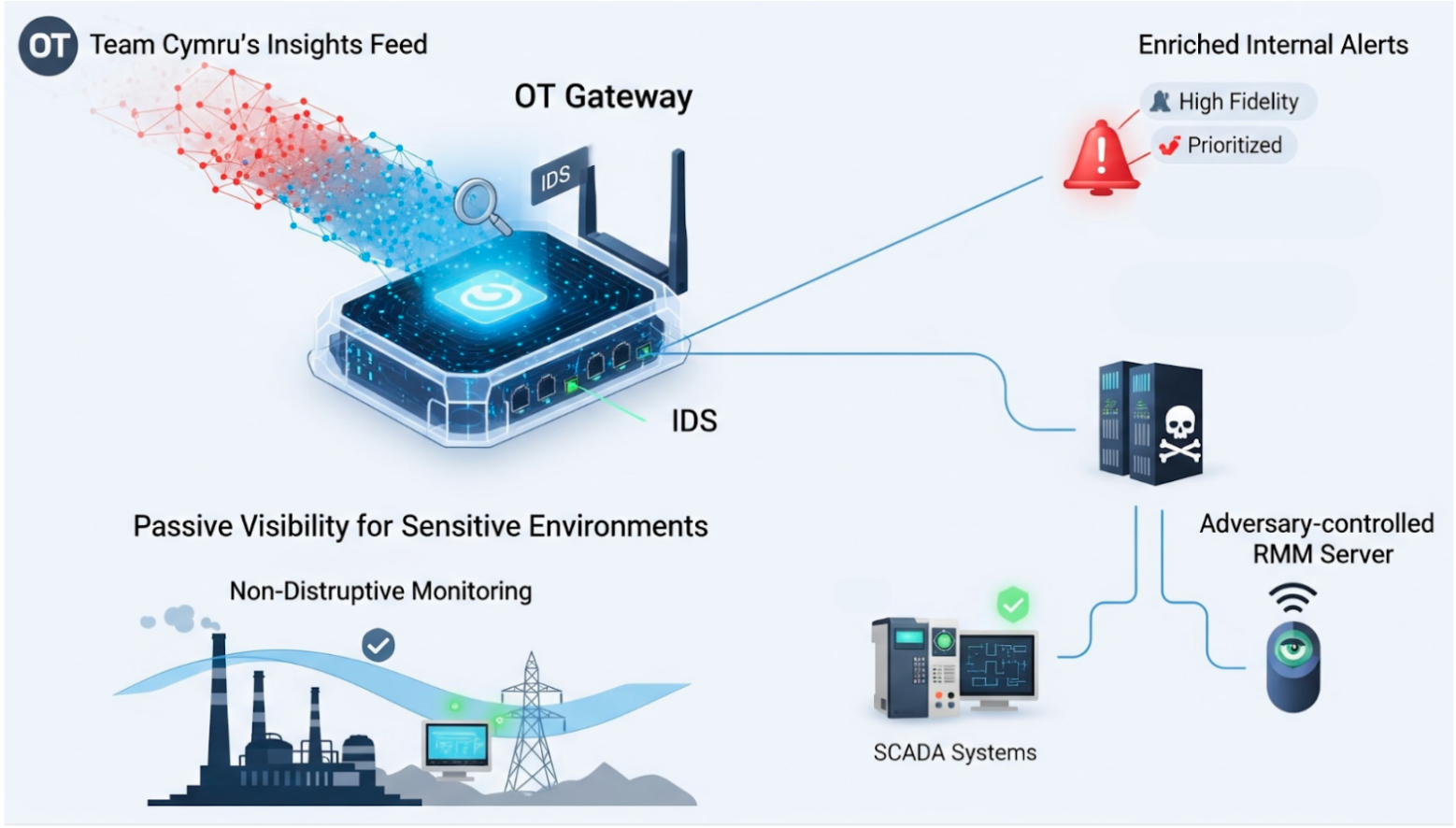
Team Cymru's Insights Feed can also enhance the detection capabilities of intrusion detection systems (IDS) in OT gateways. The Insights Feed allows OT gateways to act as a more intelligent "filter" for the network.
By populating an IDS with Team Cymru's global intelligence, organizations can:
- Enrich Internal Alerts: Use external threat data to provide higher-fidelity triage for internal alerts, allowing for more accurate prioritization of potential threats.
- Identify Malicious Communications: Detect communication between the internal OT network and unpatched or risky external IPs, such as those linked to Command and Control (C2) infrastructure or adversary-controlled Remote Monitoring and Management (RMM) servers.
Another critical challenge in OT is the risk of active scanning disrupting legacy or sensitive equipment like PLCs and SCADA systems. Through Team Cymru, defenders can gain passive visibility for those sensitive environments:
- Non-Disruptive Monitoring: An IDS integration provides passive visibility, which is essential for remote facilities where active security probes could cause operational downtime.
Government Advice
Based on the recent UK National Cyber Security Centre (NCSC) guidance and the historical data from the CITEPS tracker, the threat to CNI is considered extremely real, increasingly likely, and requires immediate, high-priority action beyond standard cybersecurity measures. The NCSC explicitly states that within the current environment of geopolitical instability and rapid technological advancement, "it is feasible that highly capable threat actors would target the UK’s CNI to cause major disruption"
The reality of this threat is supported by the CITEPS tracker, which documents a clear evolution from sporadic incidents to "critical" attacks that physically destroy infrastructure (e.g., Stuxnet destroying centrifuges) or threaten human safety (e.g., TRITON targeting safety systems). The priority level has shifted because standard incident response plans (such as those for phishing or data breaches) are no longer sufficient. Organizations must prepare for attacks that aim to "shut down critical services," "erase or corrupt data," or "damage physical systems".
Following the NCSC’s secure connectivity principles, organizations should "limit the exposure" of their connectivity and "harden the OT boundary" to reduce the attack surface. Crucially, you cannot defend what you cannot see.
Conclusion: Hardening the OT Boundary with Global Network Telemetry
The threat to Critical National Infrastructure (CNI) from sophisticated Industrial Control System (ICS) and Operational Technology (OT) adversaries has clearly evolved from a theoretical risk to an "extremely real" and "increasingly likely" one, demanding immediate, high-priority action beyond standard IT security practices. These incidents confirm that adversaries are pre-positioning themselves months in advance to deliver disruptive and potentially life-threatening kinetic effects.
The fundamental challenge, as reinforced by the UK NCSC guidance, is visibility. As OT environments connect to modern networks, organizations cannot defend what they cannot see. Closing these critical blind spots requires treating external exposure as an intelligence problem, not just a configuration issue.
Team Cymru’s capabilities provide the essential external visibility needed to address this evolving threat. By focusing on the earlier stages of the MITRE ATT&CK framework for ICS, organizations can proactively identify and track malicious external infrastructure, such as Operational Relay Boxes (ORBs), and other hosted threat actor systems.
Tools like Scout and the Insights Feed enable defenders to:
- Help Close Visibility Gaps: Monitor sensitive OT environments non-disruptively using Netflow data.
- Harden the Boundary: Discover and pinpoint internet-exposed ICS devices before adversaries do.
- Enrich Detection: Enhance intrusion detection systems (IDS) with global intelligence for higher-fidelity alert triage.
Ultimately, preventing a sophisticated CNI campaign depends on tracking the adversary’s intent as far "left of boom" as you can. By embracing Team Cymru’s external threat intelligence and continuous visibility, organizations can successfully limit their exposure, harden the OT boundary, and burn the adversary’s bridge before they can cross it to deliver disruption.

.png)
.png)
.png)