

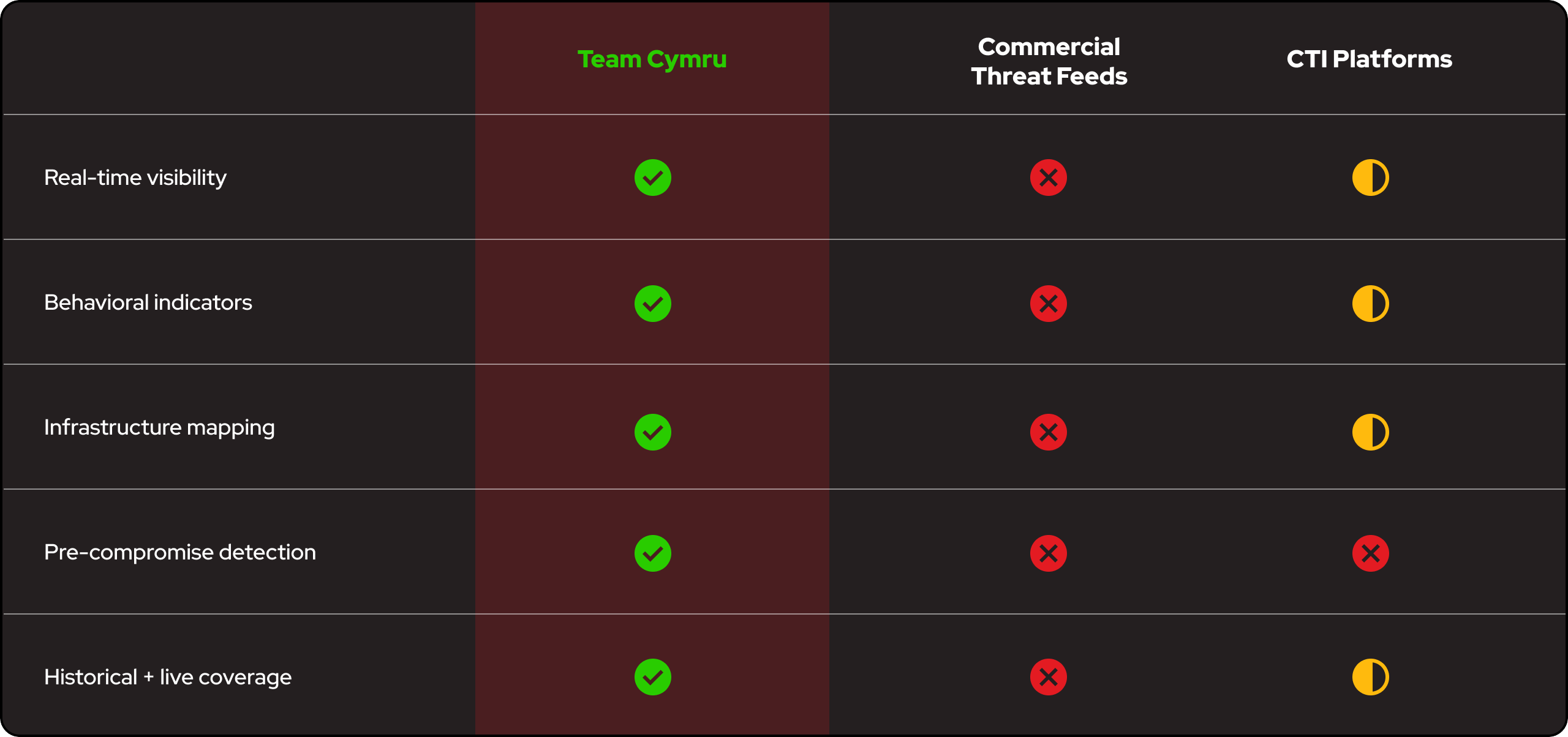
Most commercial threat intelligence feeds rely on “finished” intelligence that is outdated, incomplete, and littered with vendor interpretation/bias. This limits the effectiveness of your SIEM, SOAR, and TIP systems, leaving risky blind spots, dulling the power of your security stack, and reducing ROI.
Unlock the power of your SIEM, SOAR, and TIP systems by powering them with raw telemetry from 700+ validated global NetFlow sources.
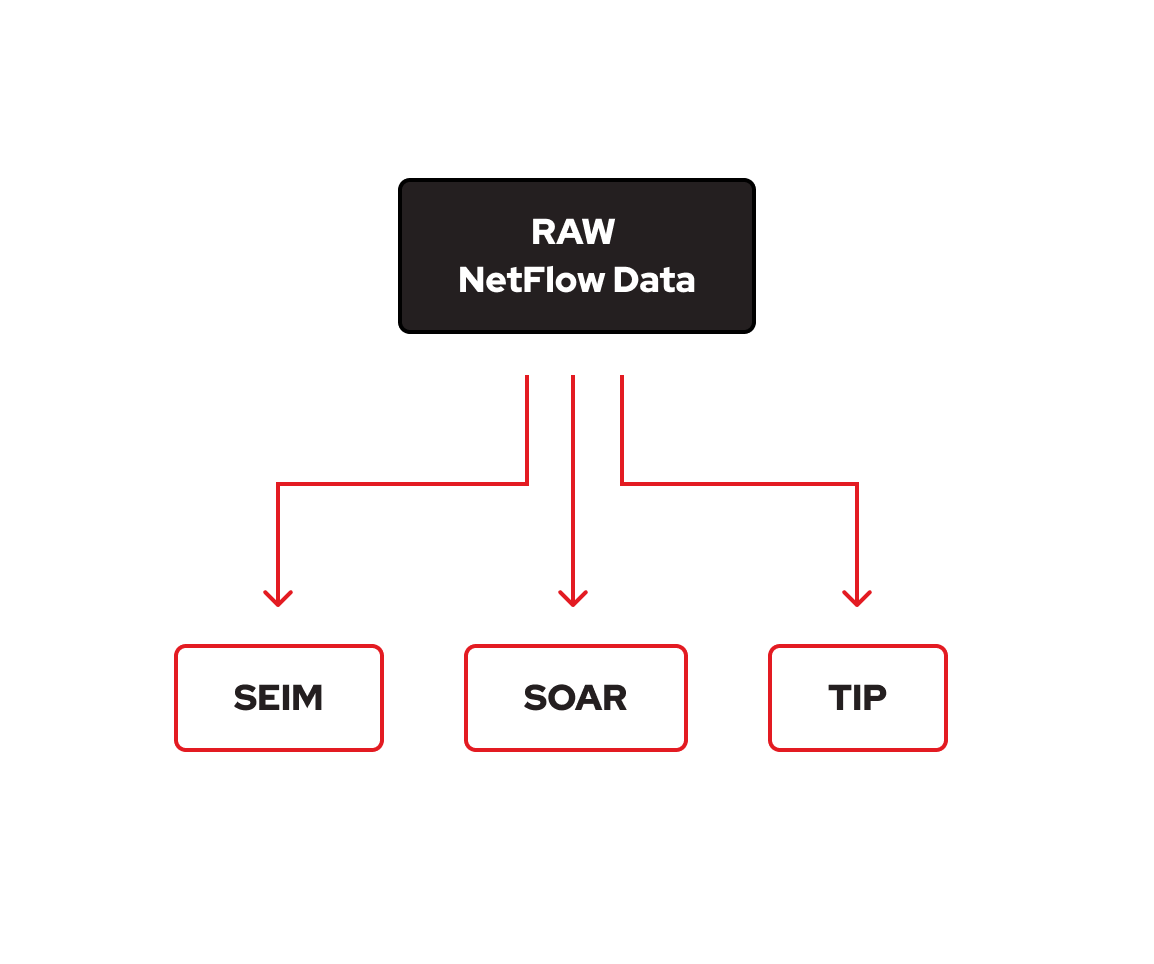





See threat activity as it happens, instead of relying on delayed, partial, or pre-processed feeds.

Get a complete view of attacker behavior, not just IOCs, so your team can proactively disrupt threats.

Map command-and-control, reconnaissance, staging, and callback activity across attacker infrastructure.

Trigger automated blocks on malicious IPs and infrastructure to stop threats before they reach your network.

Add context to alerts with C2 activity details, giving analysts faster access to actionable intelligence.

Link alerts from multiple systems by mapping shared infrastructure to uncover broader attack patterns.

Threat feed integrations spot reconnaissance activity before attackers gain a foothold in your environment.

Enhance threat intelligence platform scoring with real-time behavioral and infrastructure attributes.

Validate malicious activity before triggering automated remediation workflows.

Enrich alerts, reduce false positives, and accelerate response time.

Automate high-confidence blocking actions to stop threats faster.

Correlate infrastructure across campaigns and tools to map threat landscapes.

Know immediately when threat actors start surveilling, probing, and mapping your infrastructure for attack access points.
Explore Use Cases
Gain visibility into your extended vendor ecosystem, identifying risky connections, exposed services, and potential attack vectors.
Explore Use Cases
Visualize attacker infrastructure and malware campaigns to see how threats are connected across the internet.
Explore Use Cases
Reconstruct the full attack chain from first recon to current activities, using decades of flow data.
Explore Use CasesSee why Team Cymru is the leader in real-time data integrations that enhance your SIEM, SOAR, and TIP systems with global NetFlow visibility.