
Critical breach evidence disappears fast, making data-driven root cause analysis a complex challenge for DFIR teams.
Only NetFlow preserves all original network activity. But most organizations rely on just a handful of NetFlow streams. Complete incident reconstruction requires maximum global NetFlow visibility, which only Team Cymru provides.
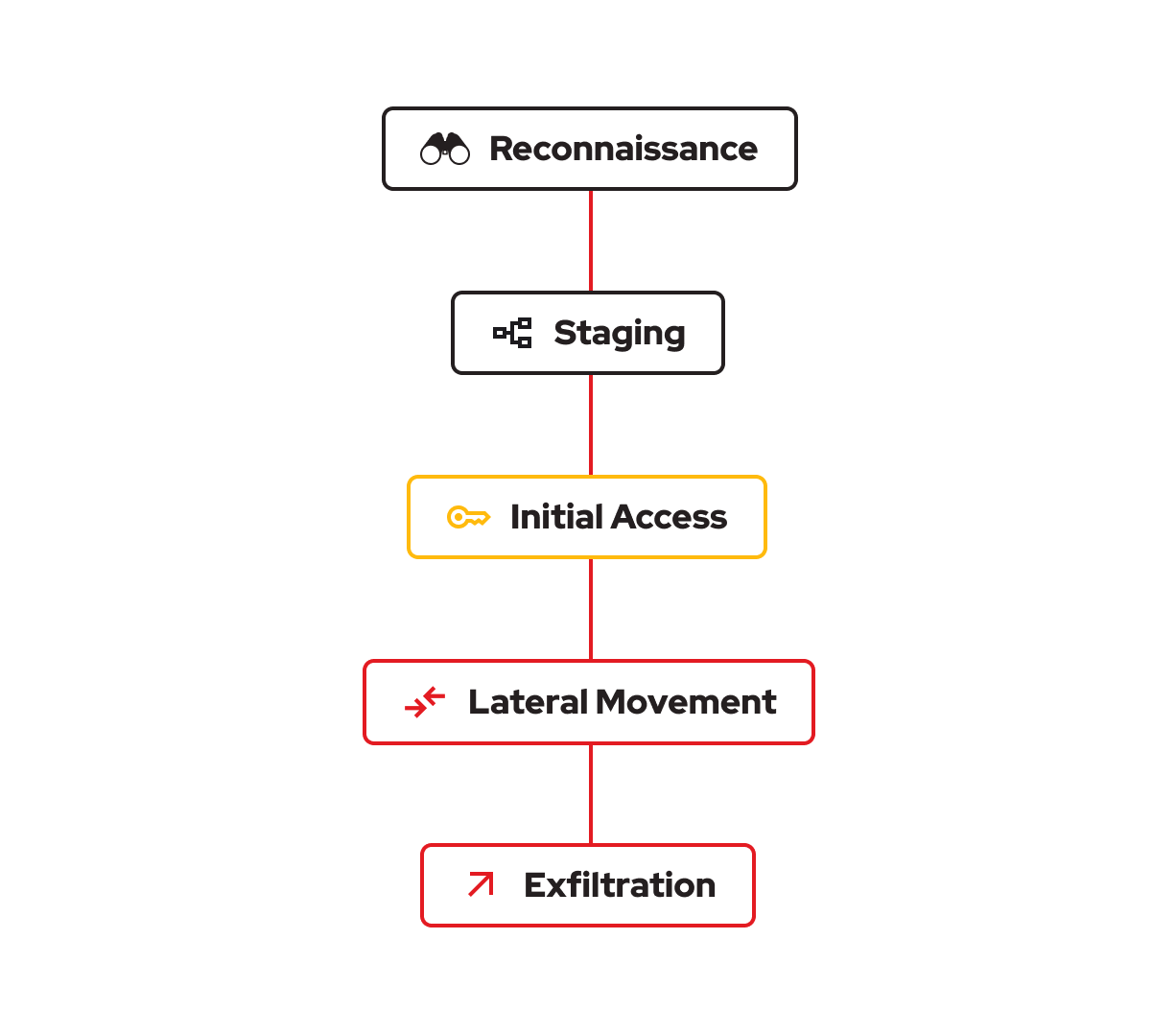
Track intrusions across every phase with 700+ global NetFlow sources powering every step of your forensic network analysis

Recon to initial access sequences

Beaconing and command paths

Staging to compromise progression

Data movement and exit paths

See months to years of NetFlow for full campaign context

Track fallback nodes, C2 rotations, and operator changes

Uncover prior recon and failed exploit attempts

Reveal infrastructure staged during threat reconnaissance, in advance of active use.
Surface the earliest attempts to gain access to blind spots in your environment.

Know exactly when compromised hosts first reached out to malicious infrastructure.

Track movements between cloud, hybrid, on‑prem systems, and your entire supply chain.

Connect incidents to broader malware and botnet operations.

Compare past activity patterns against what’s unfolding now—in real time.
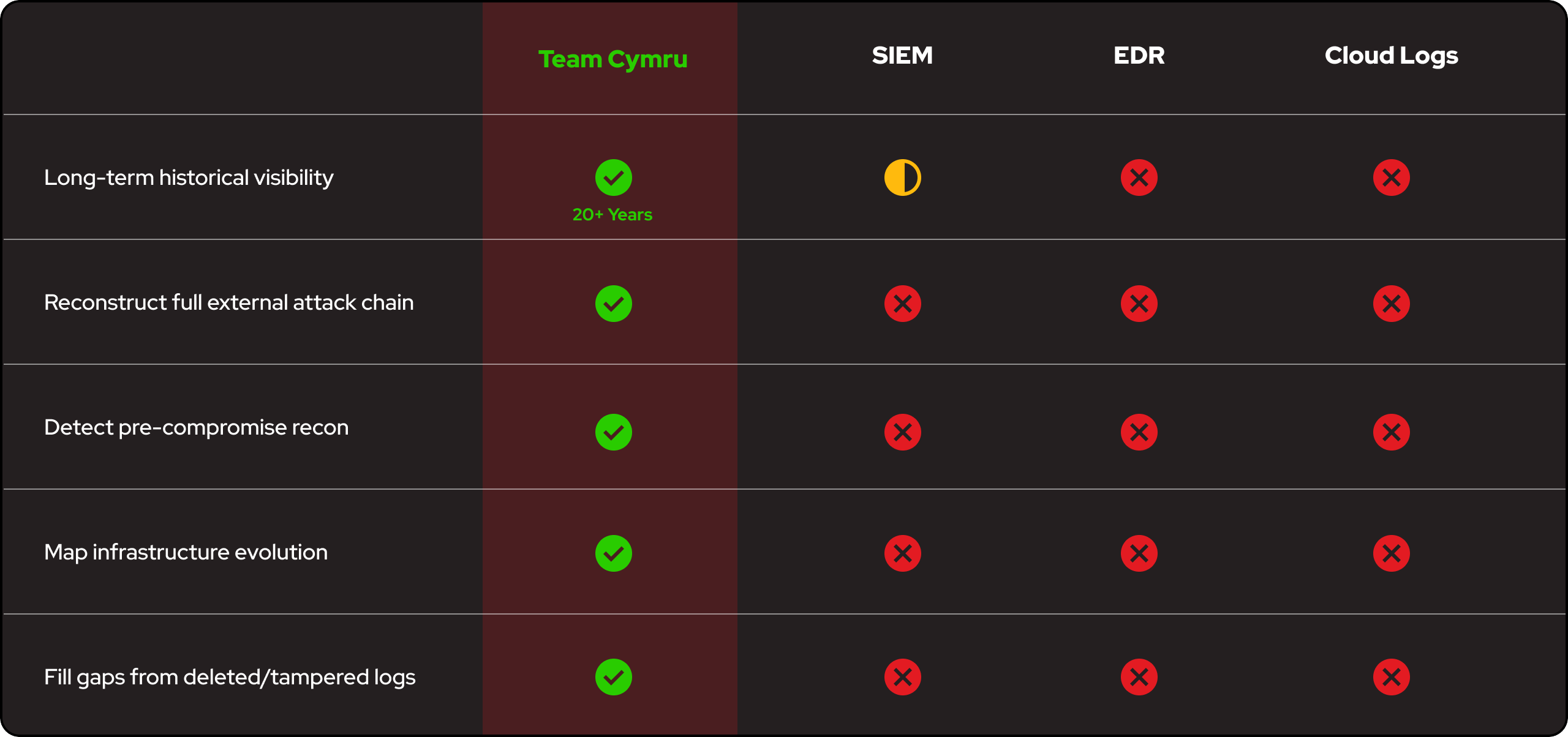

Validate attack timelines while conducting a data-driven root cause analysis.

Spot missed detections and track actor infrastructure patterns.

Trace campaign lineage and understand infrastructure evolution.

Know immediately when threat actors start surveilling, probing, and mapping your infrastructure for attack access points.
Explore Use Cases
Gain visibility into your extended vendor ecosystem, identifying risky connections, exposed services, and potential attack vectors.
Explore Use Cases
Visualize attacker infrastructure and malware campaigns to see how threats are connected across the internet.
Explore Use Cases
Stream real-time NetFlow data directly into existing security stack to accelerate detection, investigation, and response.
Explore Use CasesDefend your organization with historical and real-time threat visibility.