Scout + OpenCTI
Bridge the gap between static indicators and live infrastructure tracking.
Operationalize Team Cymru's Pure Signal™ directly within OpenCTI.

Unified Threat Intelligence & Infrastructure Tracking
Team Cymru and Filigran have partnered to enable security teams to move beyond static blocklists. By integrating Team Cymru's Scout capabilities, OpenCTI users can now access the world's largest ocean of external threat telemetry directly within their TIP.
This integration unifies Deep Enrichment for rapid incident response and Proactive Threat Hunting for identifying unknown infrastructure. Analysts can now enrich observables with unique traffic patterns, generate high-fidelity indicators based on advanced queries, and visualize threat trends over time.
Key Capabilities of the Scout Integration
Deep Enrichment
Enrich IPs with ASN history, open ports, X.509 certificates, and traffic relationships without leaving OpenCTI.
Proactive Hunting
Turn Scout's search engine into a dynamic indicator source. Hunt for unknown threats using behavioral queries.
Automated Playbooks
Standardize complex hunts (e.g. DPRK tracking) into automated workflows that run on a schedule.
Strategic Visualization
Build dashboards to track the velocity of specific threats, ransomware groups, and malware families.

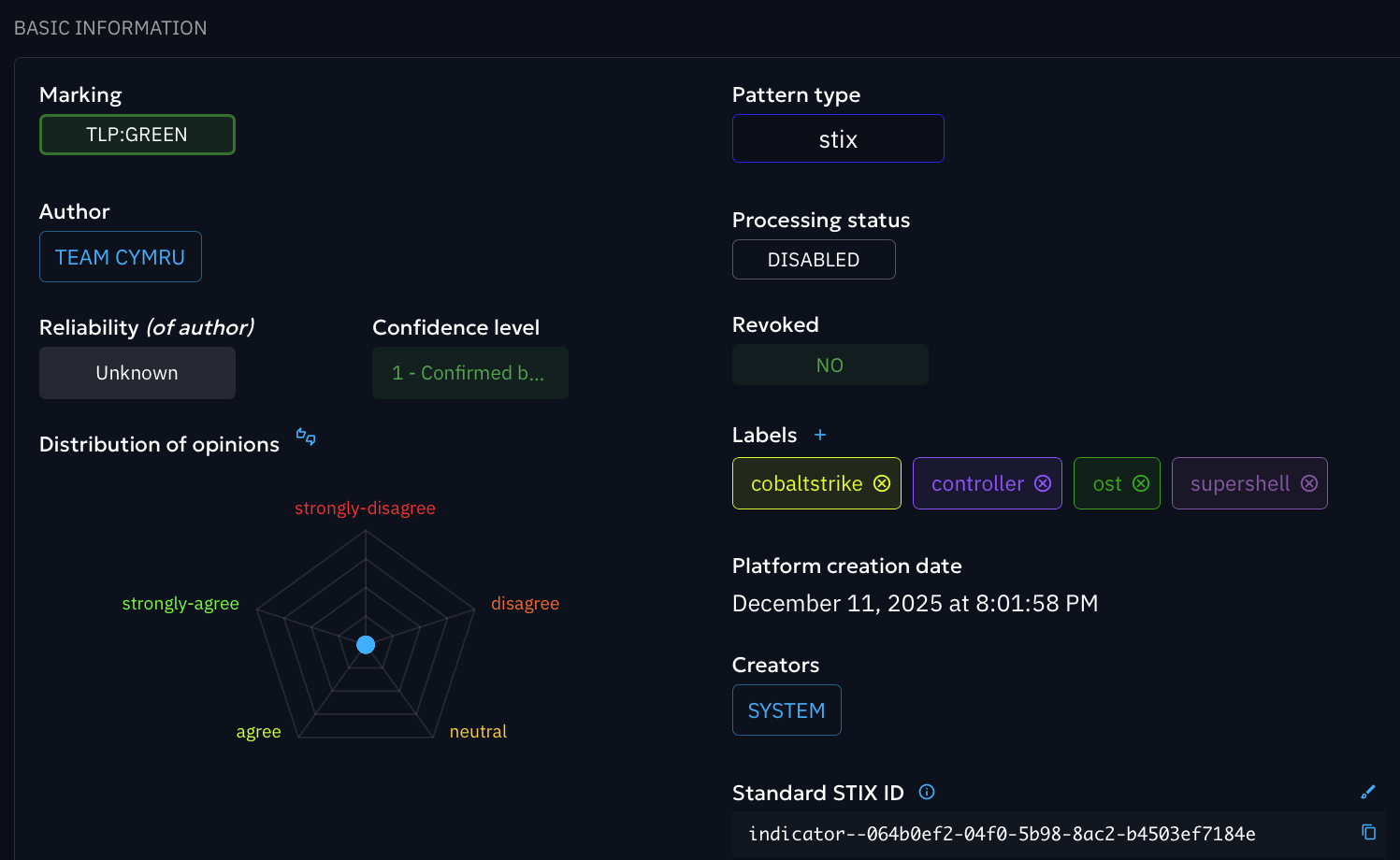
Deep Enrichment for Incident Response
Immediately enrich alerts to determine if an IP is part of an active campaign. The Scout Enrichment connector adds ASN details, open ports, and relationship data to your observables.
In Action: The screenshot demonstrates an IP address enriched within OpenCTI. Note the automatic creation of STIX relationships and the "indicators composed with this observable" section, providing immediate pivot points for analysts.

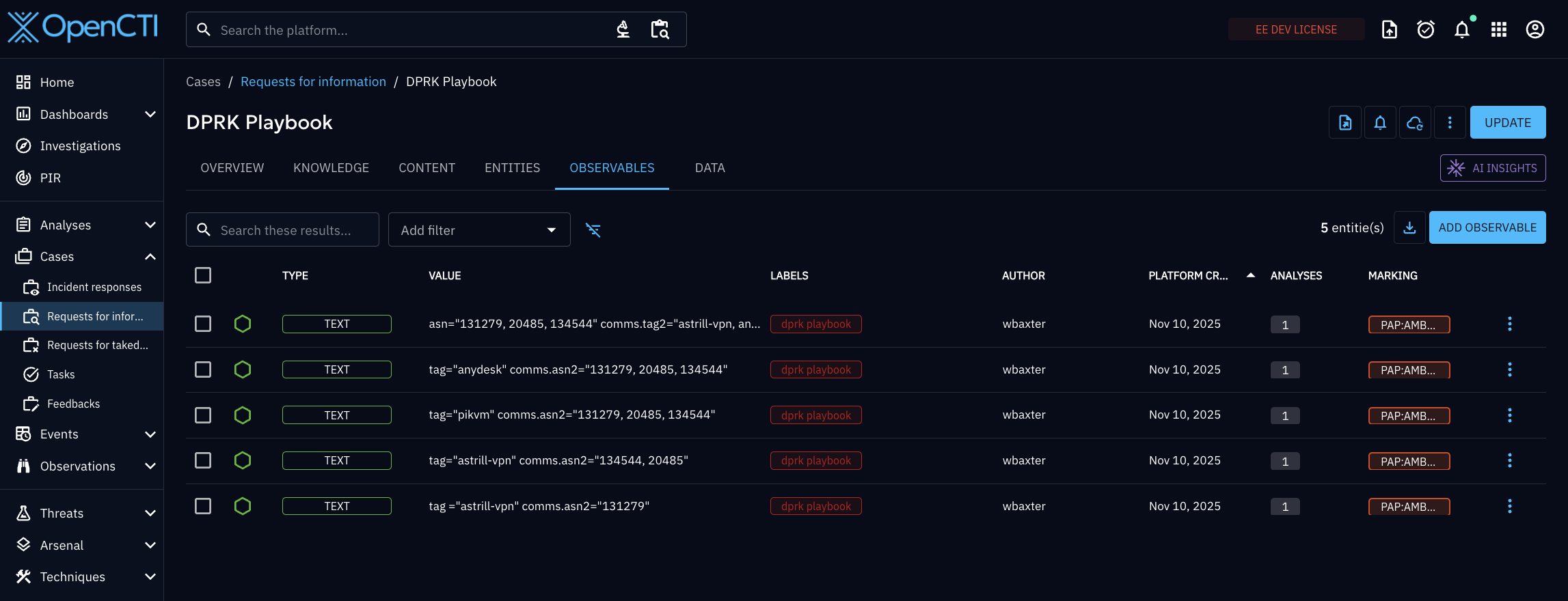
Operationalize Advanced Threat Hunting
Move beyond reactive lists. Use OpenCTI Playbooks to automate complex Scout queries that hunt for unknown infrastructure.
DPRK Use Case: The image shows a "DPRK Playbook" tracking North Korean IT workers. By running queries that look for IPs on ASNs like Star-KP or TTK communicating with Astrill VPN nodes, analysts can identify obfuscated actors before they strike.

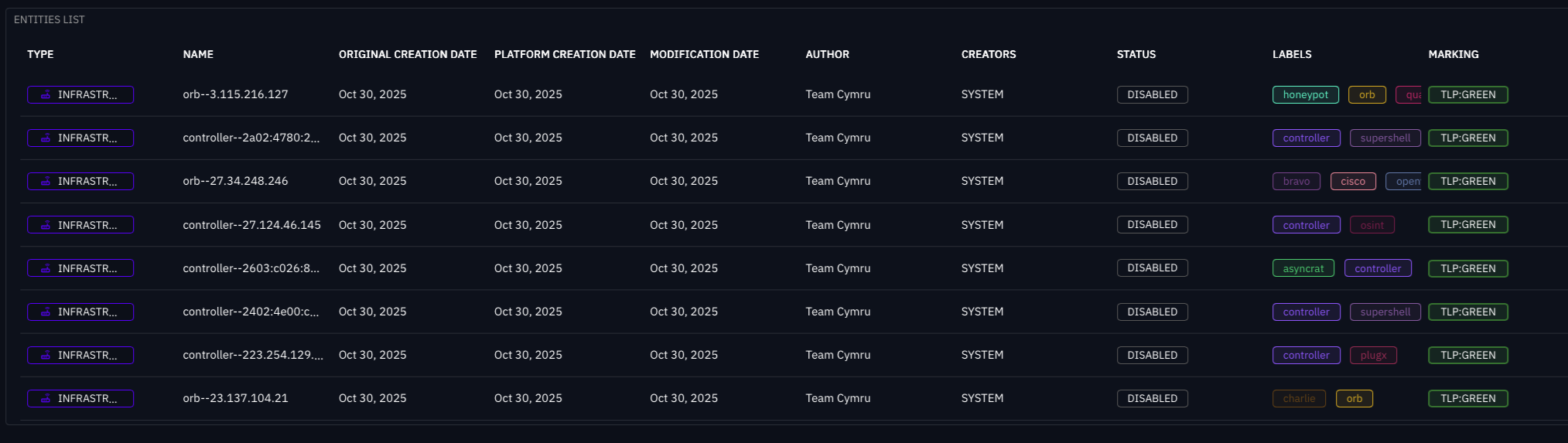
Turn Search Results into Indicators
Automatically convert Scout search results - such as lists of IPs, domains, or controllers - into STIX indicators that are ingested directly into OpenCTI for monitoring.
Automated Intelligence: Search results are ingested as entities with relevant tags derived from Team Cymru data (e.g. "controller", "vpn", "honeypot"). This ensures your platform is always populated with the latest threat infrastructure.

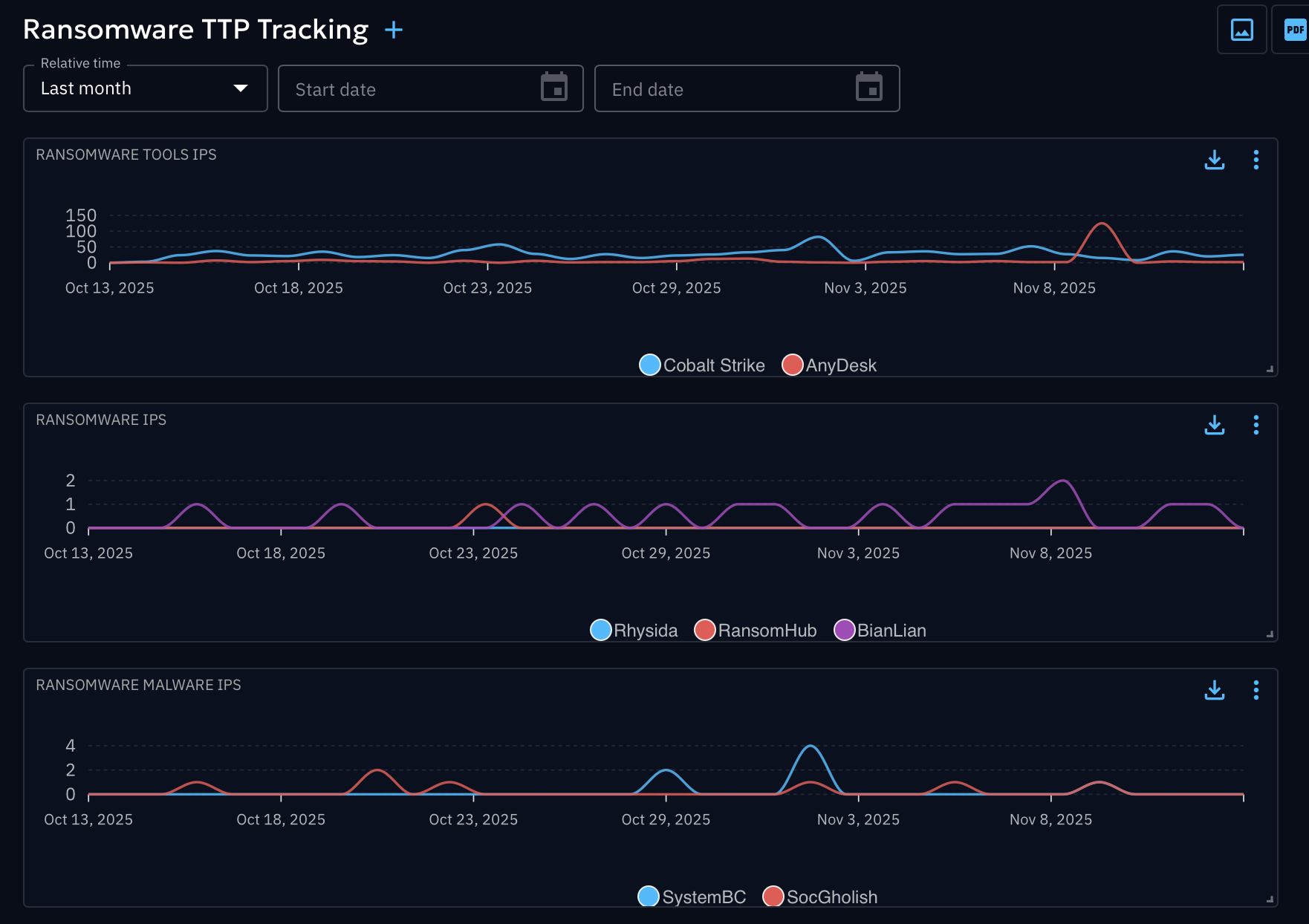
Trend Analysis & Dashboards
Visualize the velocity of threats over time. By continuously running Scout connectors, you build a historical database of infrastructure changes.
Visualize Ransomware TTPs: This dashboard tracks the volume of IPs associated with tools like "Cobalt Strike" alongside ransomware families like "Rhysida" and "BianLian", giving leaders a clear view of the threat landscape.
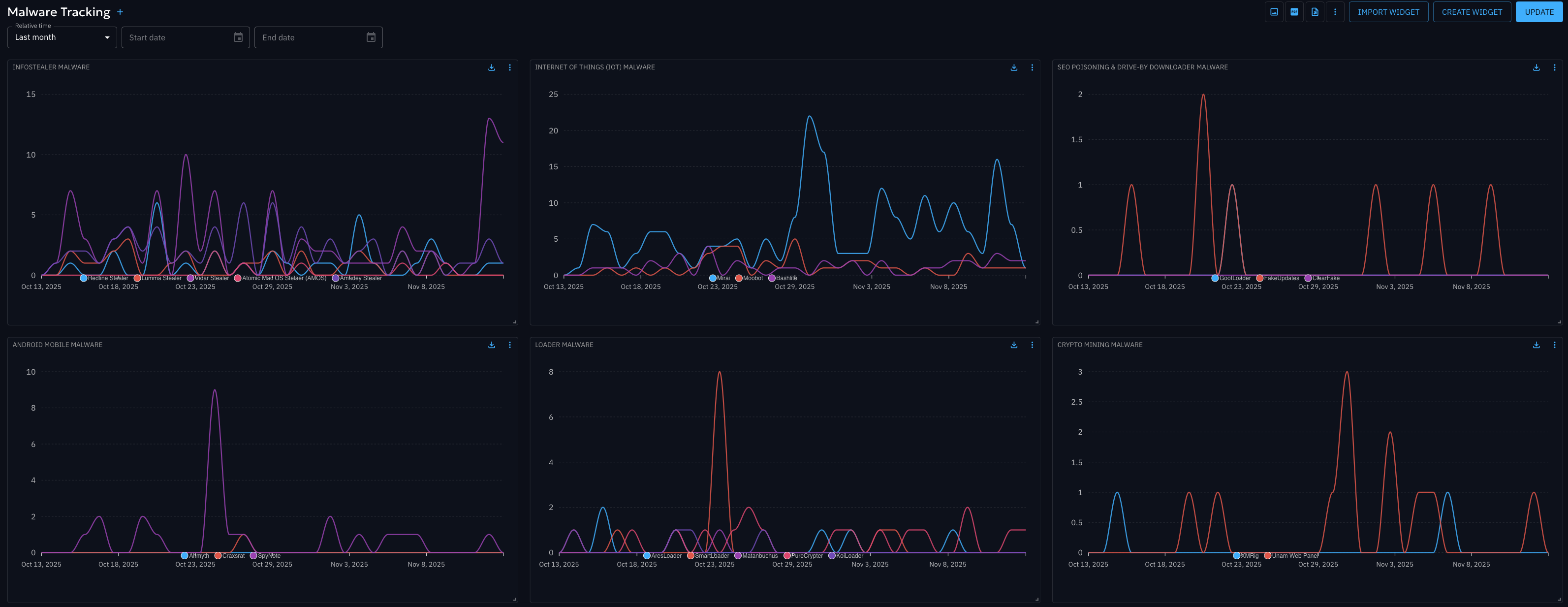
Comprehensive Malware Family Tracking
Spot spikes in specific threats, such as Infostealers or Loaders, based on the volume of infrastructure identified by Scout.
Ready to Accelerate Your Investigations?
Combine the power of OpenCTI with Team Cymru's unrivaled Pure Signal™ data. Operationalize your threat intelligence today.