.png)
Scout + Synapse
Team Cymru's Pure Signal™ Data Ocean Enables Vertex Synapse Teams To Accelerate Threat Response

Gain Unmatched Visibility into Malicious Infrastructure
Team Cymru and The Vertex Project have partnered to empower security teams with actionable cyber threat intelligence. Vertex's Synapse Enterprise is a central intelligence system designed for analytical teams, providing seamless fusion of data across platforms.
The Synapse Power-Up for Team Cymru supercharges this analysis, allowing analysts to gain visibility into active malicious infrastructure, proactively monitor risks, and respond to threats by adding context-rich data in real-time to any investigation.
This integration leverages both Team Cymru Scout for rapid, targeted IP enrichment and Recon for bulk analysis of network and DNS data.
Key Capabilities of the Scout Integration
Immediate Data Enrichment
Get in-depth information on IP addresses for fast pivots and quick decisions during security incidents.
Accurate Incident Context
Enrich alerts with real-time threat context to make informed decisions and respond accordingly.
Fuse Disparate Data
Consolidate NetFlow, pDNS, certificate data, and 45+ datasets in one central intelligence system.
Focused, Actionable Analysis
Resolve critical questions and alerts during time-sensitive investigations with high-fidelity insights.

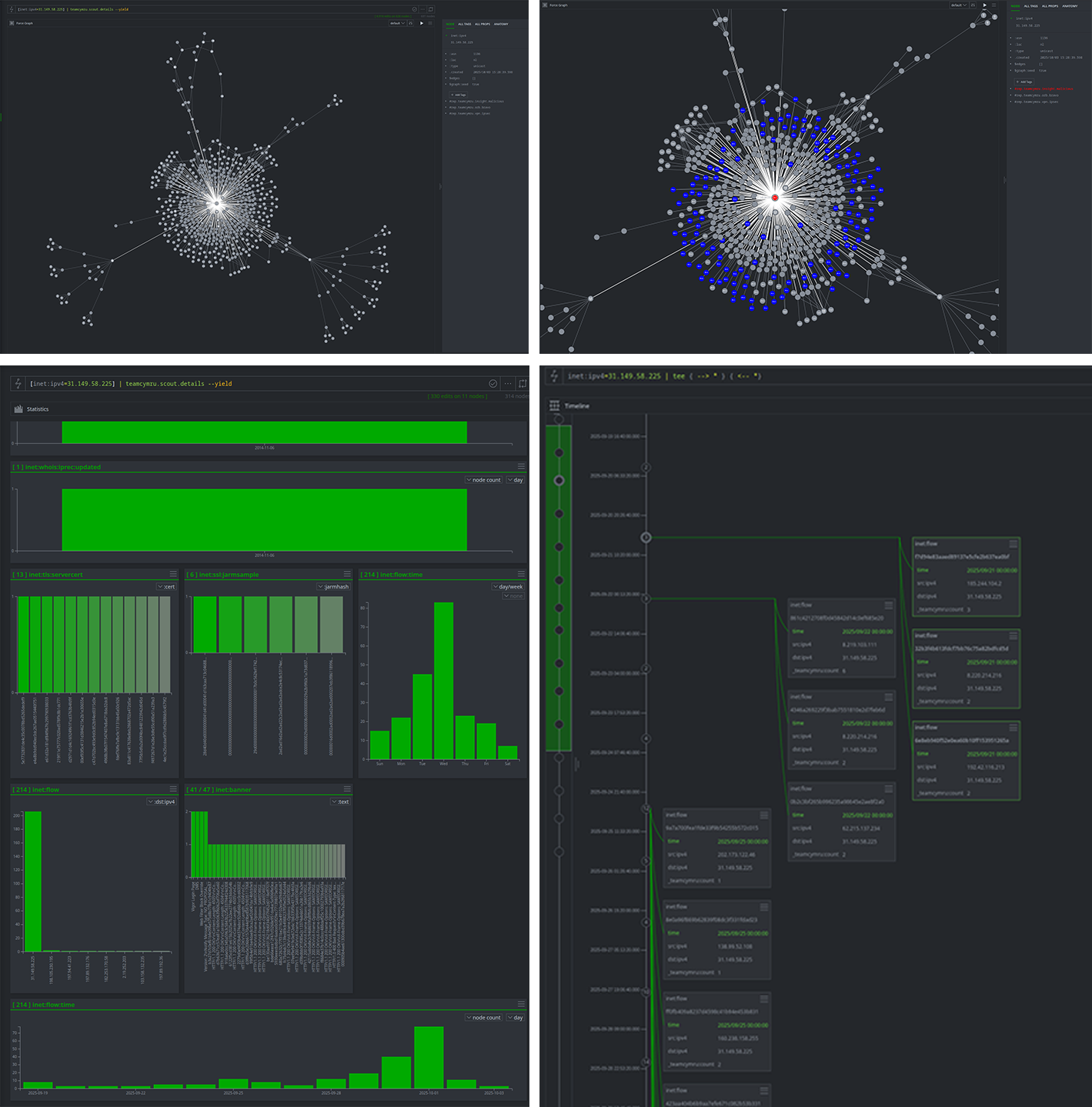
Accurate Context for Incident Response
Enrich an alert by checking if an IP address is associated with domains used in phishing campaigns that impersonate a major brand, like Microsoft.
Why It's Useful: The screenshots show a list of IPs hosting domains that contain the word "microsoft" but lack a legitimate Microsoft SSL certificate. This is a strong indicator of phishing infrastructure and provides immediate, critical context to an incident responder.

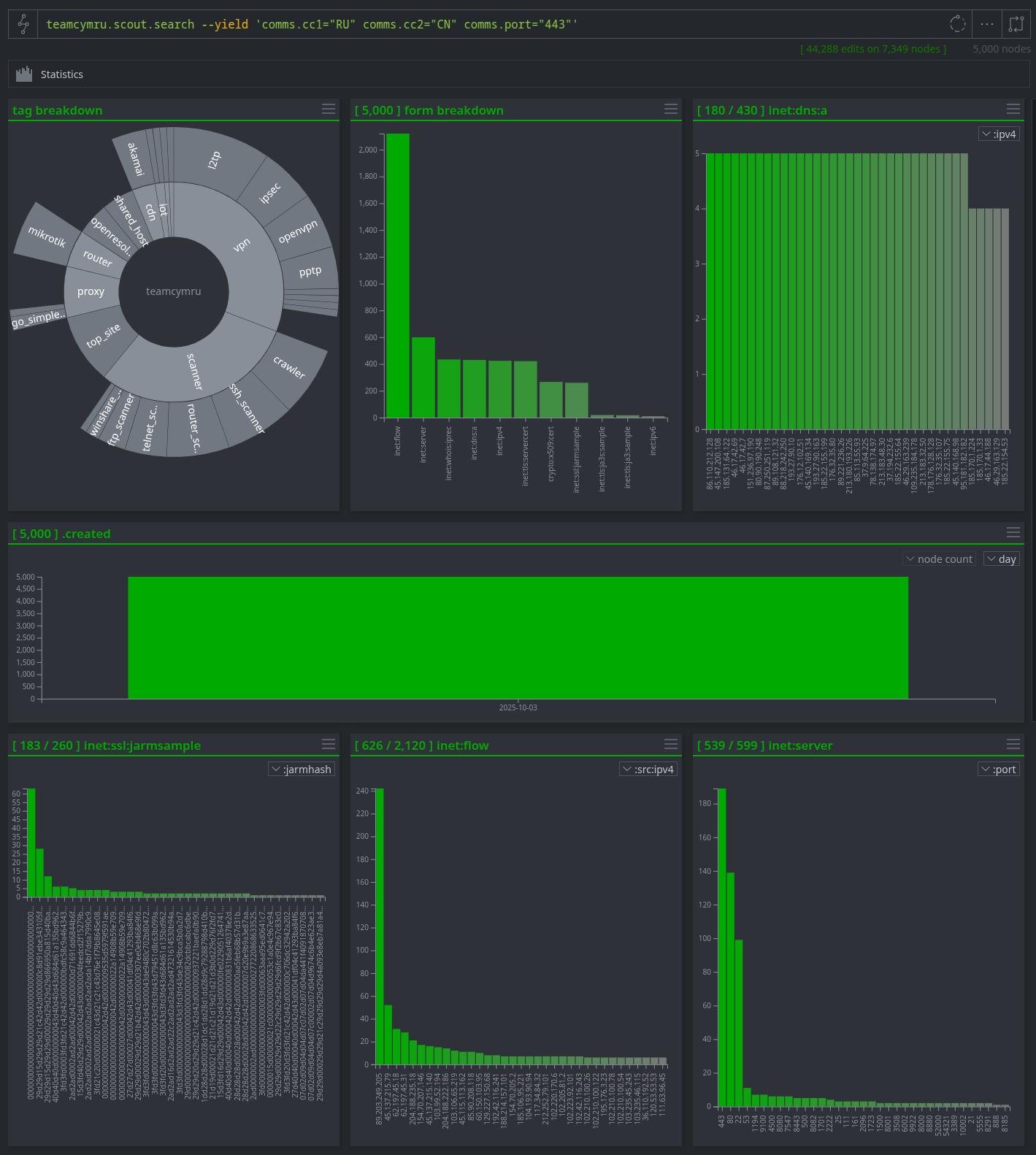
Search by Communications Patterns
Investigate relationships between networks to uncover potentially malicious activity, such as a compromised server in one country communicating with a suspicious IP in another.
Why It's Useful: This demonstrates the ability to analyze network flows and communication patterns. It helps answer, "Is this IP malicious based on its communication patterns?" by revealing its network "neighborhood," which is critical for threat hunts and international incident investigations.


Certificate Analysis for Phishing
Hunt for phishing infrastructure by identifying self-signed SSL certificates masquerading as a legitimate entity, like a "cPanel" login page. This is a common tactic used by attackers to create convincing phishing sites.
Why It's Useful: The results will list IPs with rogue certificates, directly exposing attacker infrastructure. It’s a clear and powerful demonstration of using certificate analysis to proactively hunt for threats before they are used in a campaign.

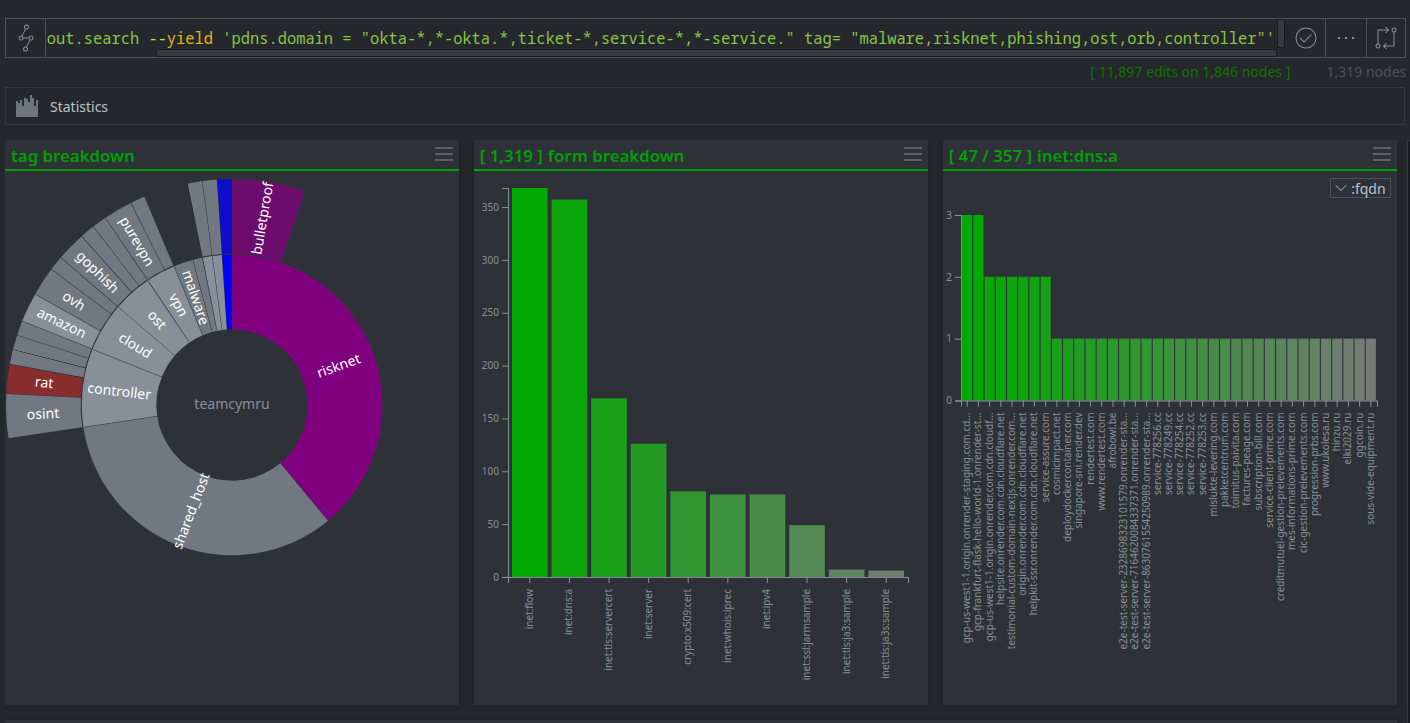
Proactive Phishing Campaign Hunting
Proactively hunt for phishing infrastructure that impersonates common corporate services like IT support tickets or Okta logins, specifically on IPs already known to be malicious.
Why It's Useful: This is a powerful example of high-confidence threat hunting. It combines suspicious naming conventions with known bad infrastructure, effectively filtering out benign results and highlighting IPs that are almost certainly malicious.
Also Integrates with Team Cymru Recon
For broader threat lanscape analysis, the Team Cymru Power Up also integrates with Recon. This enables bulk analysis of large volumes of network indicators, including network flows, passive DNS, and certificate data, to build a comprehensive historical picture of the threat landscape.
Ready to Accelerate Your Investigations?
Combine the power of Vertex Synapse with Team Cymru's unrivaled Pure Signal™ data. Get a demo today.