MediaLand Isn't Dormant: The Reality of Active OFAC-Sanctioned Infrastructure
From Sanctions to Signals: Why Compliance Requires Monitoring
Sanctions imposed by the U.S. Department of the Treasury against cybercrime-enabling infrastructure are not symbolic actions—they are indicators of active, ongoing risk. Infrastructure designated under these actions often continues to operate, host malicious services, and interact with unwitting organizations long after public announcements are made.
This report examines AS206728 (MediaLand), a bulletproof hosting network sanctioned in November 2025 for its role in supporting ransomware and other cybercriminal operations. Using a seven-day snapshot of global network telemetry (January 22–29, 2026), we assess whether this infrastructure remains active and what risks it presents today. Our findings indicate that AS206728 is neither dormant nor historical. It is actively hosting suspicious domains, conducting broad internet reconnaissance, and exhibiting traffic patterns consistent with malware operations and fraud enablement.
Investigating MediaLand (AS206728): A Sanctioned Bulletproof Hosting Network
In November 2025, the U.S. Department of the Treasury announced coordinated sanctions targeting individuals and entities that materially supported ransomware operations, including providers of bulletproof hosting (BPH) services. Among those named was MediaLand, designated for providing infrastructure intentionally designed to evade law enforcement and enable cybercriminal activity.
Reporting around these sanctions has primarily focused on individuals—such as Aleksandr Volosovik (also known as “Yalishanda”), a long-documented figure in the bulletproof hosting ecosystem—but less attention has been paid to the current operational state of the sanctioned networks themselves.
This report focuses specifically on AS206728 (MediaLand) and evaluates:
- Current hosting behavior
- Domain registration patterns
- Outbound scanning and traffic characteristics
- Indicators of ongoing malicious tradecraft

ASN Overview: AS206728 (MediaLand)
AS206728 advertises approximately 2,048 IP addresses to the public internet. From a compliance and risk perspective, this alone should raise immediate concern.
For financial services organizations and other regulated entities, any communication with OFAC-sanctioned infrastructure presents clear regulatory and reputational risk. For all other organizations, the observed activity strongly suggests that allowing inbound or outbound communication with this ASN materially increases exposure to fraud, malware, and reconnaissance activity.
Observed Suspicious Domains hosted within AS206728
Analysis identified multiple domains hosted within AS206728 that exhibit characteristics commonly associated with fraud and social engineering campaigns, including typosquatting and brand impersonation. Several domains appear designed to mimic delivery services and consumer-facing platforms—a frequent precursor to credential theft and payment fraud.
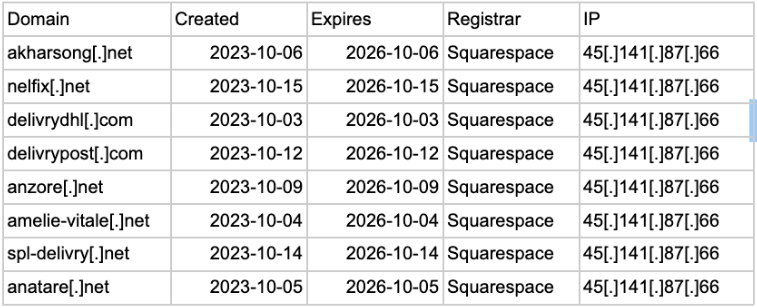
Impersonating delivery websites with typosquatting wasn’t the only unique domain practice we observed. One particular domain translated from Russian was “Death to Ukraine,” which is a particularly poignant political statement coming from the infrastructure of a sanctioned entity.
Operational Risk Indicators: Scanning, Malware Infrastructure, and Fraud Enablement
Outbound traffic analysis from AS206728 reveals patterns consistent with active reconnaissance and malware-adjacent behavior, rather than benign hosting operations.
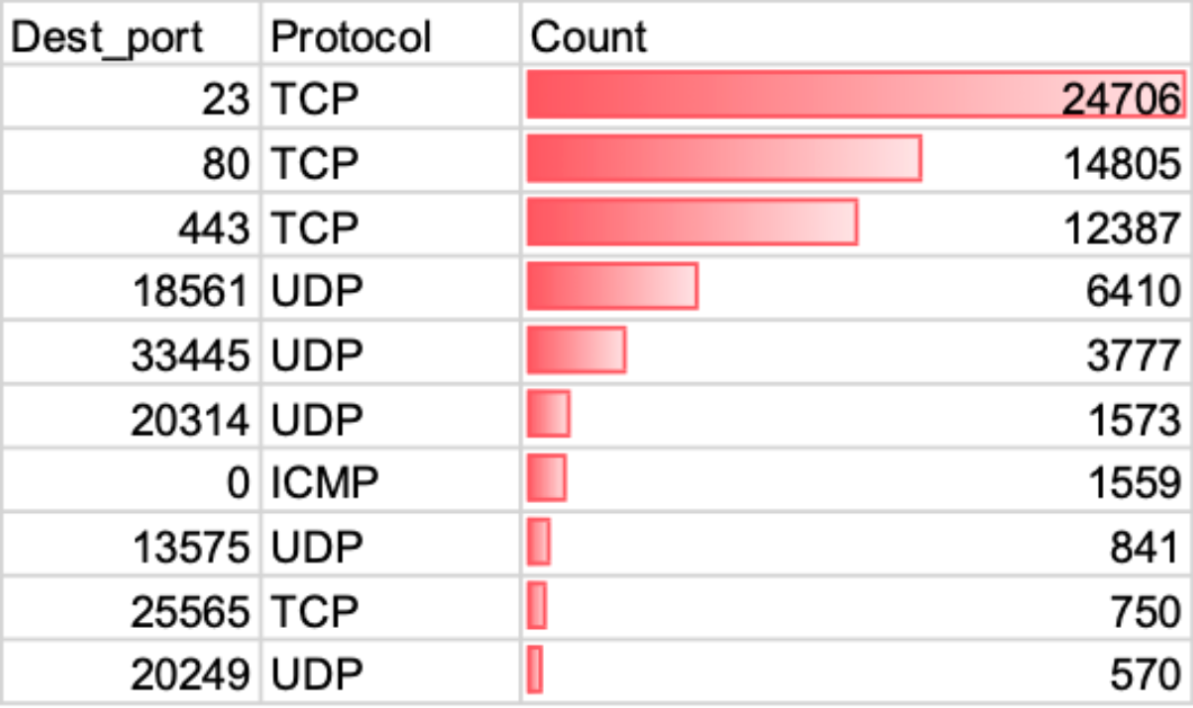
Key Observations
Port 23 (Telnet)
Telnet accounted for the highest volume of outbound traffic. Telnet remains a frequent target for mass scanning and exploitation due to its prevalence on legacy and poorly secured systems. Recent public reporting has highlighted renewed attacker interest in Telnet-exposed devices following newly disclosed vulnerabilities and botnet activity.
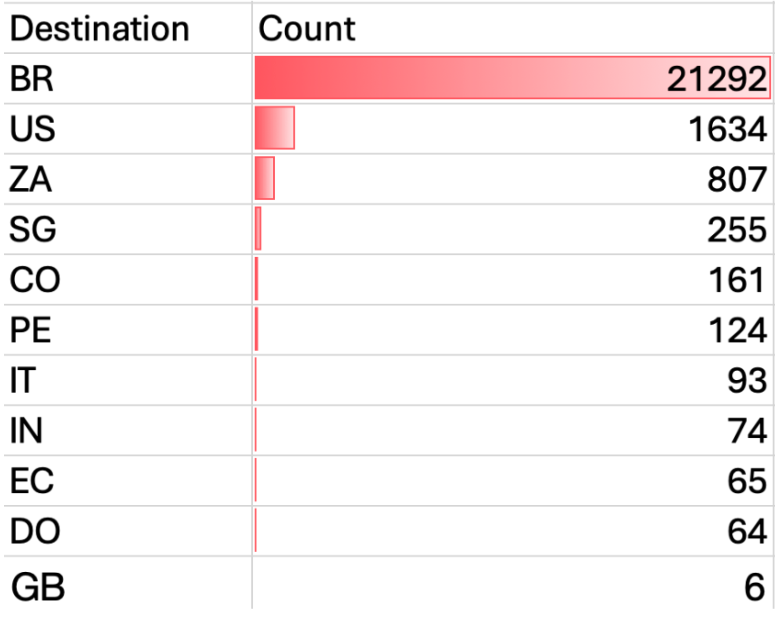
A geographic breakdown of Telnet scan destinations shows Brazil as the most heavily targeted country, suggesting large-scale, opportunistic scanning rather than targeted business communications.
Port 33445 (Tox Protocol)
Traffic to UDP port 33445 is particularly noteworthy. This port is commonly associated with Tox-based peer-to-peer command-and-control frameworks, which are frequently leveraged by malware operators to maintain resilient C2 channels. Team Cymru has previously documented this tactic in connection with malware ecosystems such as IcedID, reinforcing the relevance of this observation.
The Risk Is Not Theoretical
The presence of widespread Telnet scanning, malware-associated ports such as 33445, and impersonated domains targeting delivery and financial brands indicates that this ASN is not dormant, nor is it purely historical. It is active, opportunistic, and aligned with tradecraft that routinely precedes fraud losses and security incidents.
In practical terms, this means:
- Employees, customers, or vendors interacting with this infrastructure may already be exposed
- Legacy or misconfigured systems may be under active reconnaissance
- Fraud campaigns leveraging this hosting may already be in flight
Ignoring this traffic does not make it go away—it simply increases dwell time and reduces response options.
Final Takeaway
OFAC sanctions related to cybercrime are not abstract policy tools—they are actionable intelligence. For financial institutions, they represent an opportunity to reduce fraud, strengthen defenses, and demonstrate regulatory maturity before losses occur.
Sanctioned infrastructure that remains active is a signal that adversaries are still operating—and that someone, somewhere, is still unknowingly enabling them.
The institutions that pay attention to that signal now will be the ones best positioned to explain their decisions later.

.png)

.png)