

Supply chain security threats sit outside traditional visibility, highlighting an urgent problem: you can’t defend what you can’t see. With 90% of organizations citing third-party compromise as their top risk, external attack surface monitoring is mission critical.
Leveraging the most comprehensive collection of global NetFlow sources, Team Cymru delivers behavioral evidence of compromise across external networks, giving you maximum visibility before attackers can infiltrate your infrastructure.
We own the only real-time and global view into external supply chain compromise.
With the world’s most extensive collection of raw NetFlow data sources, Team Cymru exposes the supply chain cyber security threats that go unseen by traditional cybersecurity tools.

See which suppliers are talking to known threat actor infrastructure within minutes.

Spot scanning, staging, and C2 callback activity across global networks in real time.

Trace lateral infections and links between compromised vendors and attacker systems.

Detect C2 callbacks, scanning, and data exfiltration paths in real time.

Track threat actor infrastructure from supplier IPs to broader campaign activity.

Reveal cross-partner or vendor infections spreading laterally across networks.
Tactical clarity on supply chain cyber security threats for analysts and CISOs alike

Spot suppliers talking to known command-and-control infrastructure in real time.
Detect repeated traffic from suppliers to risky or suspicious IP ranges.

Identify probing and scanning activity originating from vendor networks.

Reveal when attacker staging systems come online in partner environments.

Track unusual lateral activity spreading across vendor ecosystems.

Monitor abrupt spikes in network flows that may indicate compromise.
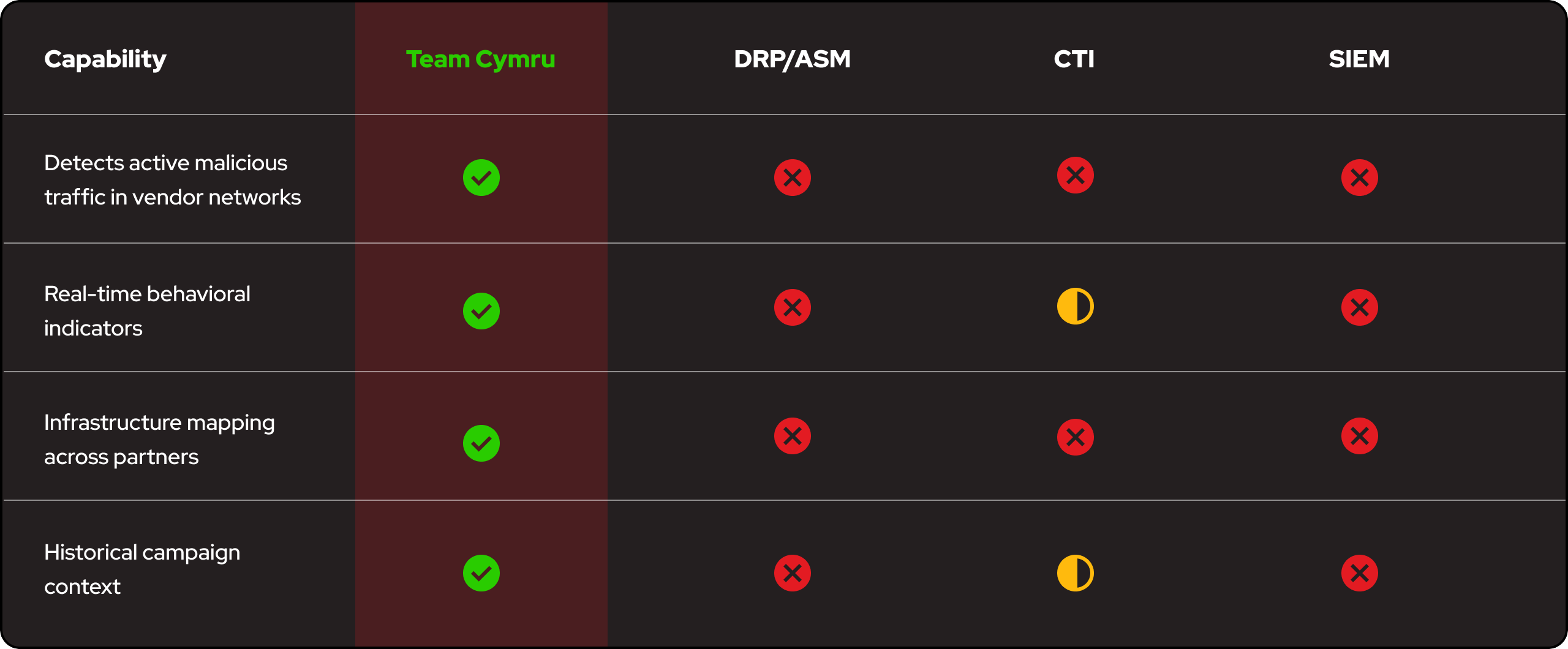
See the difference in our supply chain security threat detection capabilities.

Prioritize third-party risk in real time. Identify compromised suppliers before they become attack vectors. Validate vendor security posture with live behavioral evidence rather than static questionnaires.

Confirm supply chain security threats and map attacker infrastructure across vendor networks. Correlate real-time raw flows with historical behavior to uncover hidden attacker activity.

Build preemptive defenses to block malicious vendor communications. Detect reconnaissance, staging, and lateral movement using raw source insights instead of filtered threat assessments with inherited vendor bias.
Explore ways to leverage our NetFlow for real-time external attack surface monitoring

Know immediately when threat actors start surveilling, probing, and mapping your infrastructure for attack access points.
Explore Use Cases
Visualize attacker infrastructure and malware campaigns to see how threats are connected across the internet.
Explore Use Cases
Replay and analyze past and current network flows to uncover hidden threats and early-stage compromise.
Explore Use Cases
Stream real-time NetFlow data directly into existing security stack to accelerate detection, investigation, and response.
Explore Use CasesGain live visibility into partner and supply chain security threats with our unmatched NetFlow vendor risk monitoring