

Cyberattacks always start with network reconnaissance. Threat actors probe, scan, and map your infrastructure, looking for blind spots to penetrate. But instead of alerting you during this reconnaissance stage, traditional security tools don’t ping until attacks are already underway—far too late.
NetFlow data exposes threat reconnaissance in real time, giving you the visibility to detect and disrupt attacks before damage occurs.

Identify systematic probing and repeated hits on specific ports, hosts, and network segments as attackers map your environment.

Spot slow, distributed reconnaissance patterns engineered to blend in and evade detection from SIEM and EDR tools.

See staging infrastructure the minute it comes online—often the earliest sign an attacker is preparing for initial access.

Reveal beaconing, callback tests, and abnormal paths between known C2 infrastructure and unknown external IPs.

See recon attempts across the worldwide Internet, not just inside your perimeter.

Get live visibility into network reconnaissance as it’s happening—not after the fact.

Amplify investigative context by tracing any recon event over months or years.

Expose large-scale scanning operations targeting specific industries or technologies.
Reveal attackers preparing lateral movement through unusual connections between internal hosts.

Spot the early stages of credential-harvesting operations as they prepare to gather log-in credentials.

Identify reconnaissance probes aimed at critical systems and sensitive data stores.

Show how threat actors map cloud services and resources to locate potential attack paths.

Track beaconing and callback activity from endpoints to inactive command-and-control infrastructure.
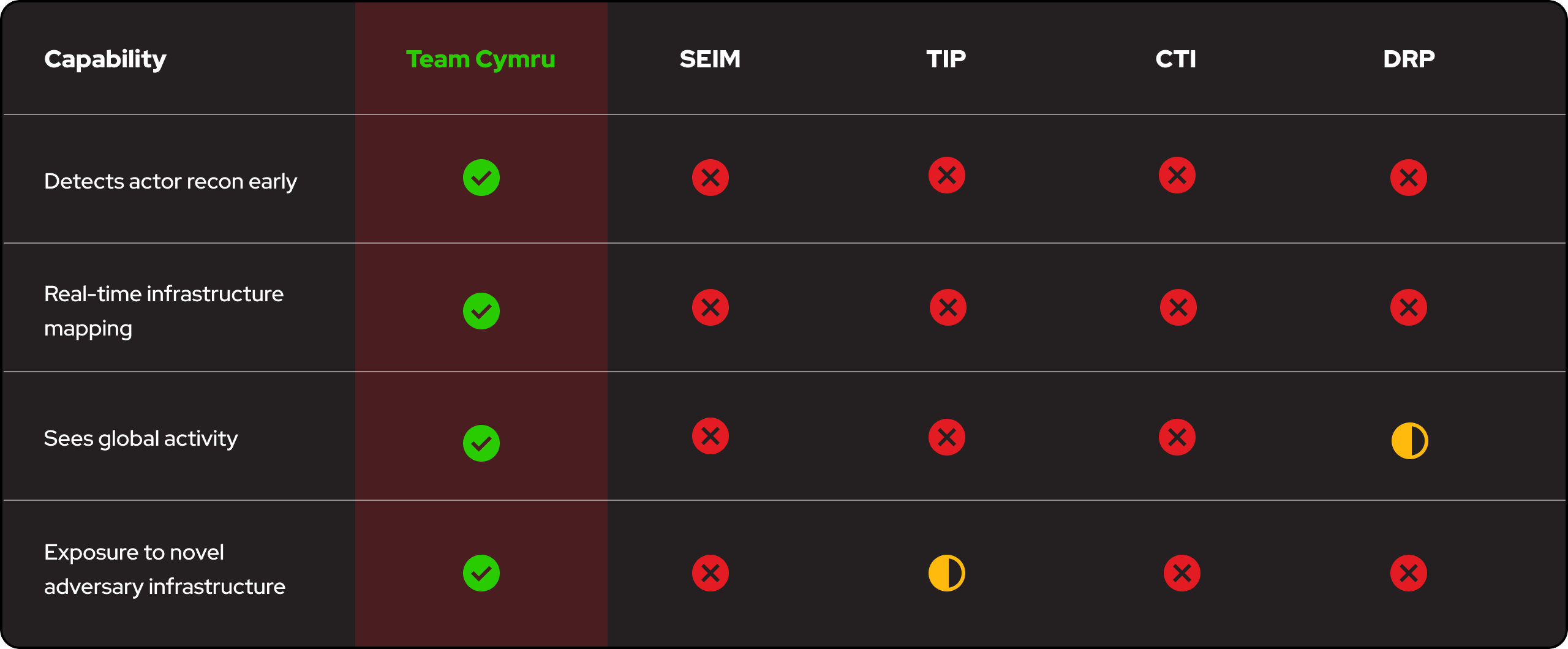

Identify and block malicious infrastructure before exploits launch.

Prioritize alerts based on verified pre-compromise reconnaissance signals.

Attribute operators and track campaigns during early development.
External Threat Reconnaissance is one part of a broader visibility advantage only available with Team Cymru. Explore how the same raw NetFlow vantage point powers additional high-impact use cases.

Locate malicious connections within supplier and partner networks in real time.
Explore Use Cases
Reconstruct the full attack chain from first recon to current activities, using decades of flow data.
Explore Use Cases
Attribute callbacks to operator infrastructure and track malware ecosystems over time.
Explore Use Cases
Automate blocking and enrichment with raw NetFlow monitoring for cyber threat defense.
Explore Use CasesDiscover how our comprehensive collection of raw NetFlow data reveals network reconnaissance long before attackers invade your perimeter.