

Malware threat intelligence no longer relies on a single file. Instead, it requires visibility into a distributed ecosystem. Threat actors operate across staging servers, proxy nodes, bulletproof hosting, and multiple C2 families.
Team Cymru delivers real-time, global NetFlow visibility across the entire malware and botnet ecosystem. See into external networks so you can detect, map, and disrupt attacks before they reach your environment.





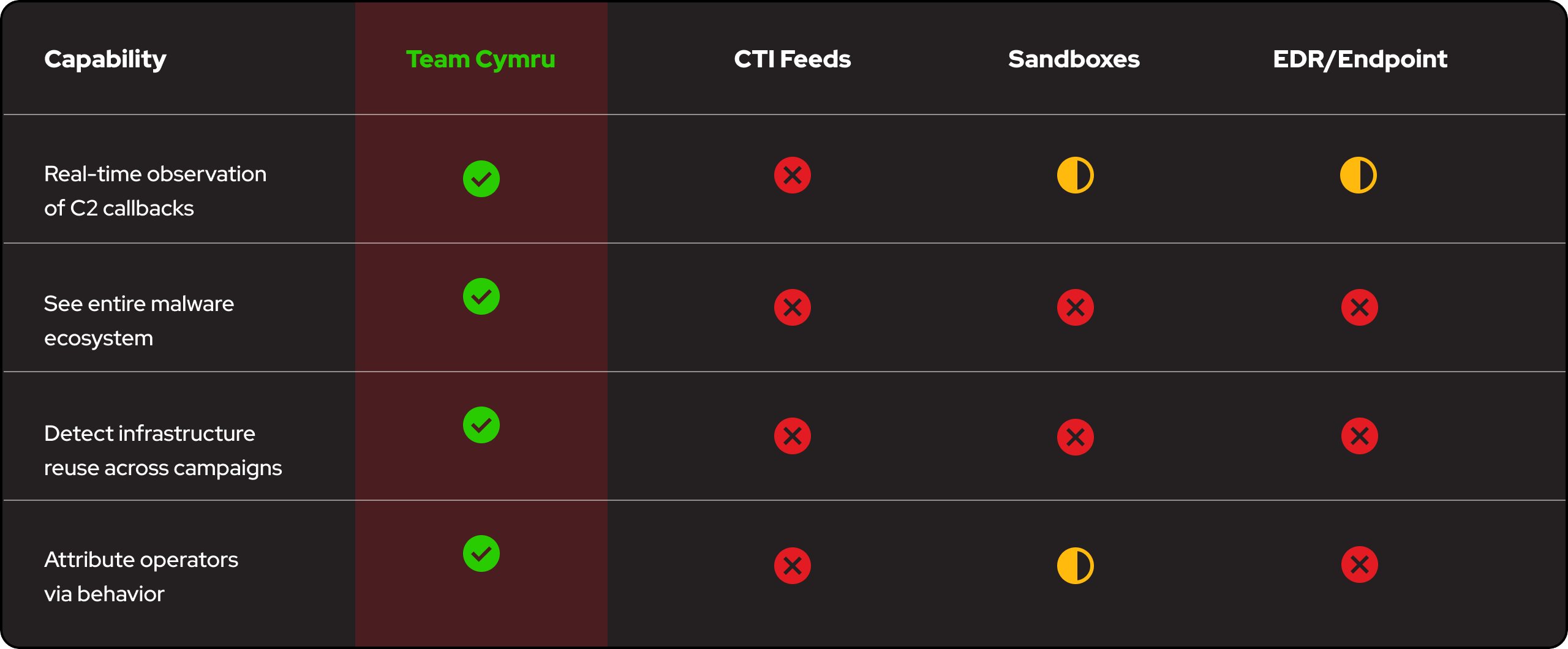
Uncover the structural visibility that NetFlow provides for botnet malware analysis across ecosystems.

Follow flow-level activity from compromised endpoints to the operator infrastructure behind them, revealing command execution, beaconing rhythms, and early pivot behavior.

Surface the relationships between C2 servers, proxy chains, and staging infrastructure, uncovering the backbone nodes that support multiple malware families.

Observe how botnet components span regions and providers, mapping cross‑geography infrastructure patterns that traditional threat feeds never reveal.

Analyze timing, frequency, and “phone-home” paths from infected hosts to understand attacker communication behavior.

Reveal multi-node command-and-control setups, including proxies, redirectors, and fallback hosts supporting malware operations.

Map connections between malware families and shared operators to uncover broader campaign-level infrastructure relationships.
Get tactical malware threat intelligence insights, with continuous visibility as threat actor behavior evolves.

Spot newly activated command-and-control nodes as they come online in real time.

Observe sudden surges in beaconing and communication from infected hosts.

Track malware families extending operations into new regions and networks.

Identify backup servers and alternate pathways used when primary infrastructure fails.

Reveal attempts by malware to move laterally across internal or partner networks.

Expose shared nodes and resources used across multiple malware families and campaigns.
See what makes our botnet malware analysis capabilities different.

Leverage global NetFlow to understand attacker infrastructure, relationships, and emerging malware campaigns.

Use raw telemetry to identify and prevent malware and botnets from infiltrating your network.

Investigate incidents with complete internal and external visibility into attacker behavior and network compromise.

Know immediately when threat actors start surveilling, probing, and mapping your infrastructure for attack access points.
Explore Use Cases
Gain visibility into your extended vendor ecosystem, identifying risky connections, exposed services, and potential attack vectors.
Explore Use Cases
Replay and analyze past and current network flows to uncover hidden threats and early-stage compromise.
Explore Use Cases
Stream real-time NetFlow data directly into existing security stack to accelerate detection, investigation, and response.
Explore Use CasesSee the full picture of malware and botnets activity to stay ahead of emerging threats.