The Indictment Is the IOC: Using Legal Records to Hunt DPRK Remote Workers
Recently, it was reported a Maryland man had been indicted and sentenced to 15 months in prison for his role in participating in a scheme to facilitate fake IT workers from North Korea. Indictments in cases such as these are goldmines of data for threat hunting.
The Criminal Complaint → Threat Hunt
As researchers, criminal complaints provide a wealth of information. Coupled with Team Cymru’s unique global telemetry, we used the information in these documents to identify attributes for hunting suspicious activity.
From this paragraph in the indictment, we identified a few specific attributes on which to focus our search. IPs with these attributes are not inherently malicious; however, they do possess qualities that could warrant further investigation.
We searched for IPs with the following attributes:
- US-based
- Communicating with Slack
- Operating AnyDesk
- Communicating with Russia
We used the folowing query:
cc="US" tag="anydesk" comms.tag="slack" | comms.cc="RU"
This query returned a list of eight IP addresses to further investigate.

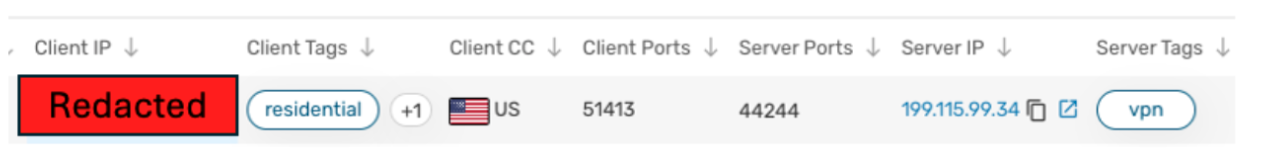
We identified one of these IPs as residential.
Focusing on the residential IP, we conducted further investigations to determine if there were any communications to identified Astrill VPN assets;indeed, we found one. Google’s Mandiant previously identified fake IT workers from the DPRK using Astrill VPN.
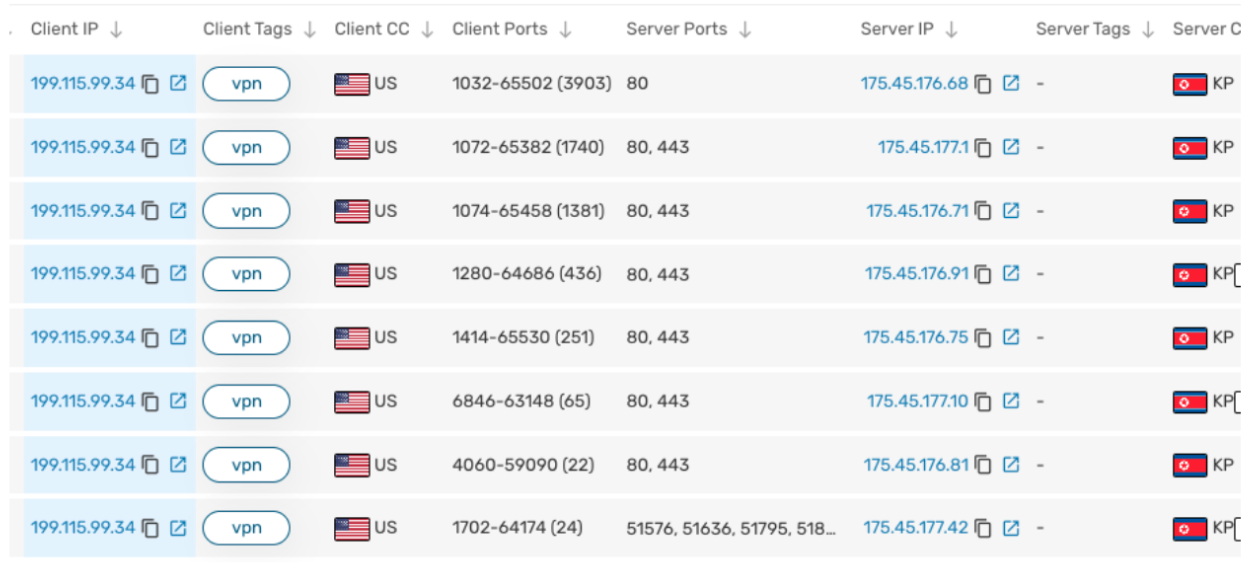
From here, we pivoted to the Astrill VPN to determine if that IP was communicating with any North Korean IPs. We immediately found eight different North Korean IPs that were communicating with it.
What does this mean?
None of the indicators above are remarkable on their own.
Slack traffic is normal. AnyDesk is everywhere. Residential IPs talk to commercial VPNs every day. Even Russia-based traffic, in isolation, is not a smoking gun.
What makes this activity stand out is the combination of it all in one spot. The totality of the circumstances.
Court documents sometimes give us details of the tactics, techniques, and procedures (TTPs) with alarming precision.
Global telemetry lets us test those narratives against reality, at scale, without relying on victim reporting or endpoint access.
When you combine details like those in the indictment with enough data, you stop hunting for “North Korean malware” and start hunting for North Korean behavior.
That shift matters because these operations are not noisy breaches or smash-and-grab intrusions. They are long-lived, low-friction campaigns designed to blend into Western corporate IT environments. They succeed precisely because every individual technical signal looks reasonable when viewed in isolation.
Threat hunting informed by court documents changes the game. It tells you what habits to look for, what tradecraft persists across campaigns, and where normal activity starts to have the hallmarks of a sanctions-evasion scheme.

.png)
.png)
.png)