Query Scout in Synapse Enterprise With New Power-Up for Team Cymru
Team Cymru’s integration with The Vertex Project makes information from the Pure Signal™ data ocean accessible to analysts working in Synapse Enterprise. This integration joins Team Cymru’s global visibility and context-rich telemetry data with the power of the Synapse Enterprise platform, allowing for frictionless analytical capabilities and a unified approach to detection and response.
By ingesting Team Cymru’s data into Synapse Enterprise, analysts can carry out powerful queries of Pure Signal™ data without ever having to leave the platform. This allows for efficient, confident decisions with a seamless analytic experience.
Sample Use Cases for Synapse Power-Up for Team Cymru
The following examples are representative of ways analysts can run Scout queries within the new Synapse Power-Up for Team Cymru.
Search by Communications Patterns
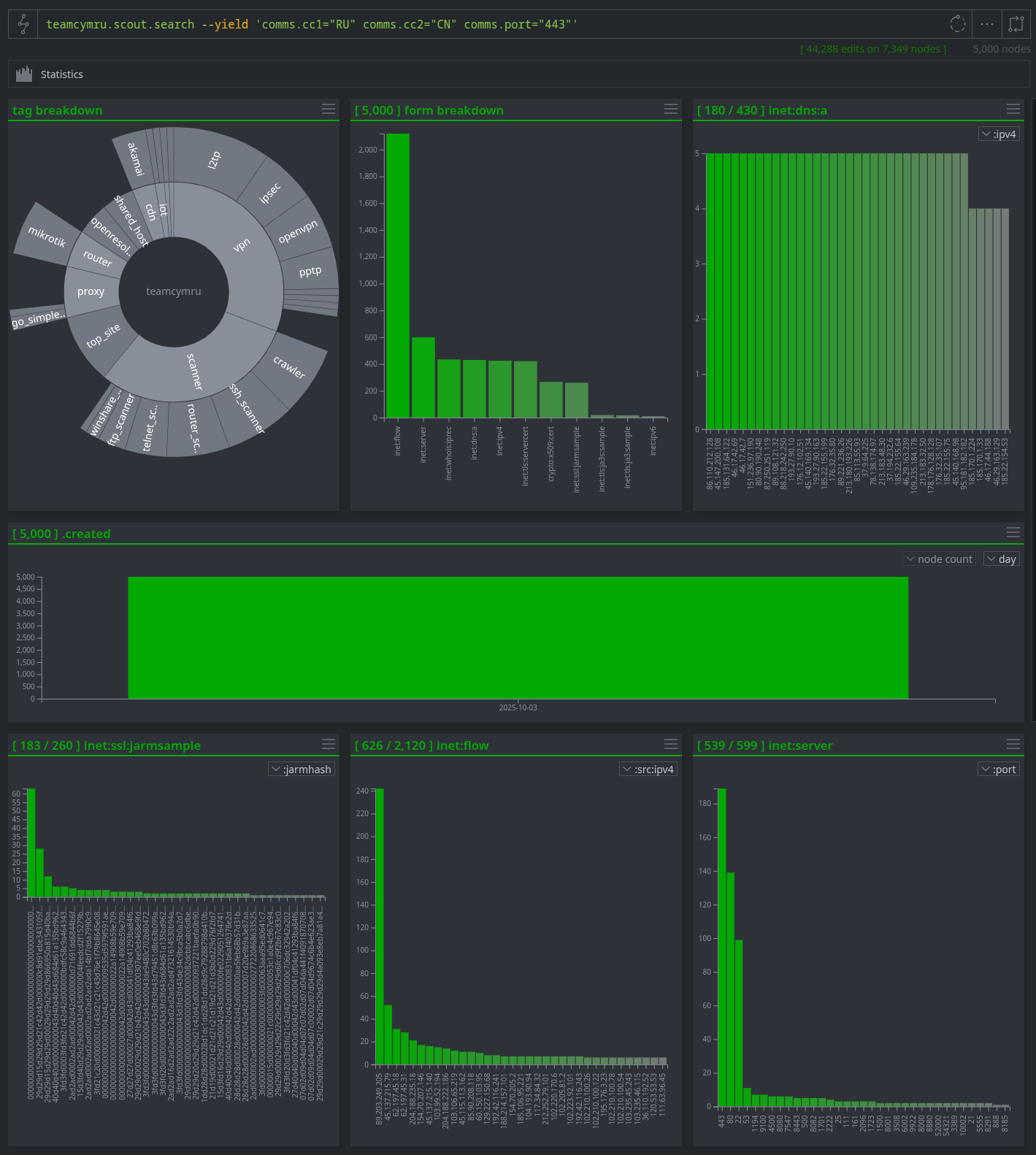
The Power-Up for Team Cymru allows for detailed investigations focused on communication patterns. For example, this sample query investigates the relationships between different networks to uncover potentially malicious activity, such as a compromised server in one country communicating with a suspicious IP in another.
- Sample query intent: Identify all communications between an IP address in Russia (RU) and an IP address in China (CN) occurring over the common C2 port 443 (HTTPS).
- Scout Query:
comms.cc1="RU" comms.cc2="CN" comms.port="443"
- Why It's Useful: During threat hunts and international incident investigations, traffic—including potentially legitimate traffic—is often scrutinized. This query analyzes network flows and communication patterns, helping to answer whether an investigated IP is malicious based on its communication patterns by revealing its network “neighborhood.”
Certificate Analysis for Phishing
Analysts can use the Power-Up for Team Cymru to hunt for phishing infrastructure by identifying self-signed SSL certificates masquerading as a legitimate entity, in this case, a generic "cPanel" login page. This is a common tactic used by attackers to create convincing phishing sites.
- Sample query intent: Uncover potential phishing sites by searching for IPs with self-signed SSL certificates where the certificate's Common Name (CN) is related to cPanel.
- Scout Query:
x509.subject.cn="*cpanel*" x509.selfsigned=true
- Why It's Useful: This query returns IPs with rogue certificates, directly exposing attacker infrastructure. Security teams can use this form of certificate analysis to proactively hunt for threats before they are used in a campaign.

Proactive Phishing Campaign Hunting
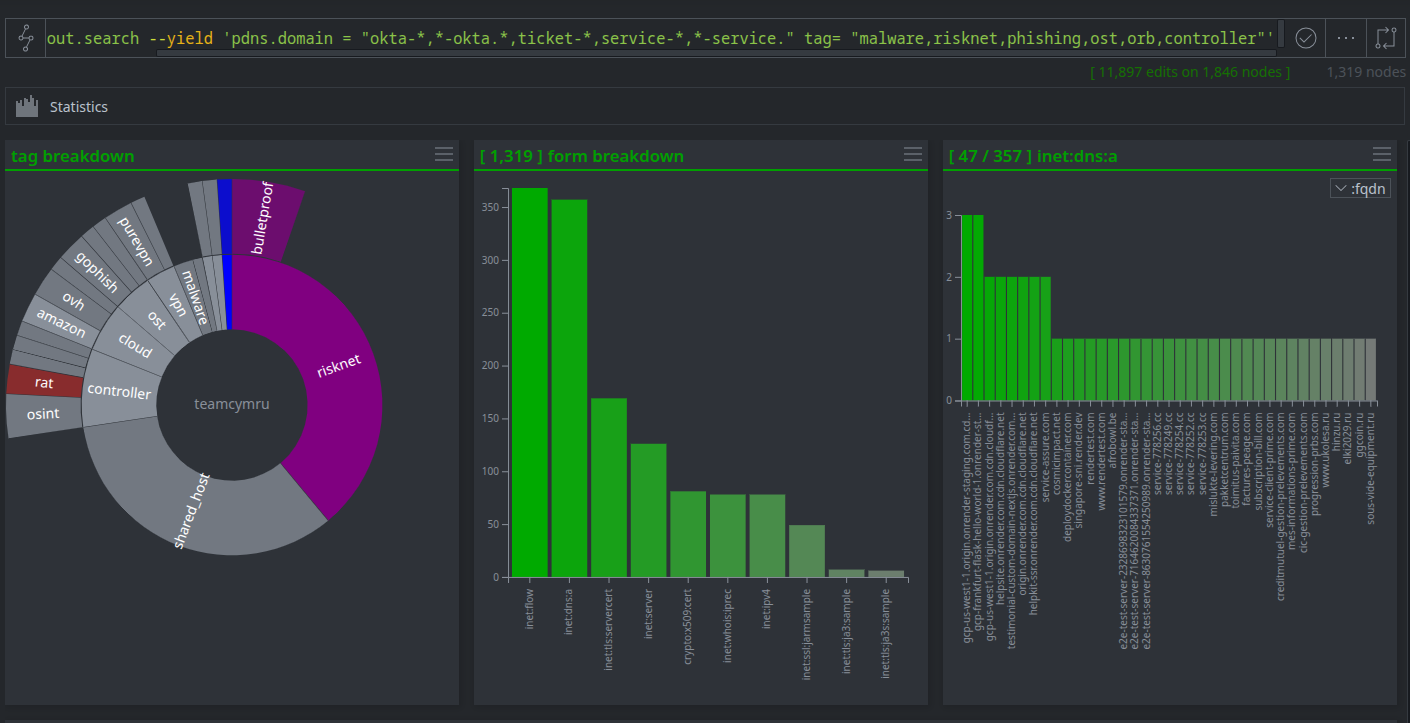
Similarly, the Power-Up for Team Cymru allows analysts to proactively hunt for phishing infrastructure. This query uncovers infrastructure impersonating common corporate services like IT support tickets or Okta logins, specifically on IPs already known to be malicious.
- Sample query intent: Find IPs with known malicious tags that are also hosting domains with keywords like "okta-", "ticket-", or "-service", which are common in corporate phishing lures.
- Scout Query:
pdns.domain = "okta-*,*-okta.*,ticket-*,service-*,*-service." tag= "malware,risknet,phishing,ost,orb,controller"
- Why It's Useful: This query allows for high-confidence threat hunting. It combines suspicious naming conventions with known bad infrastructure, effectively filtering out benign results and highlighting IPs that are almost certainly malicious. This allows security teams to stay ahead of potential phishing campaigns.
Unpacking a Malicious IP with Correlated Insights
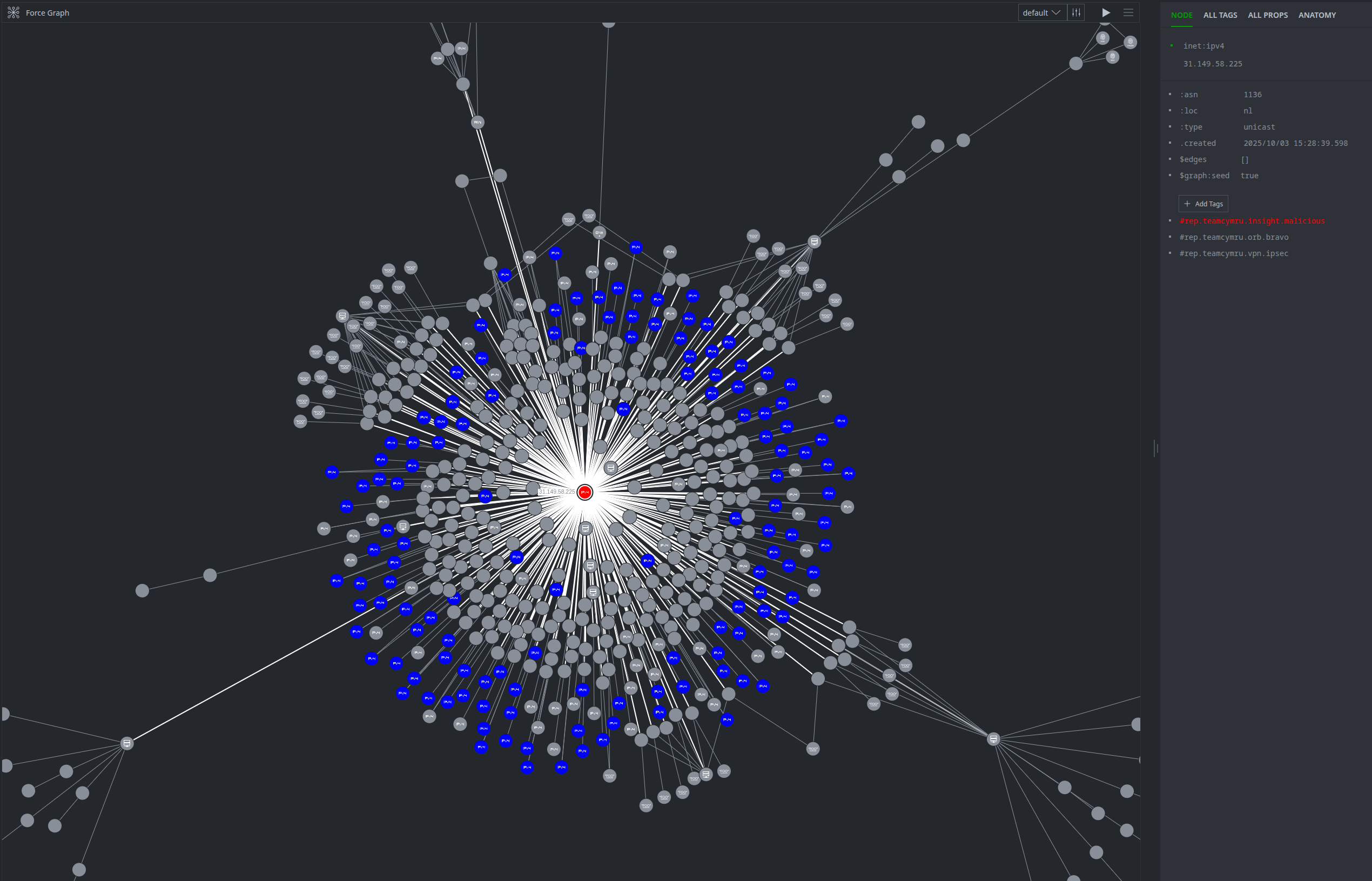
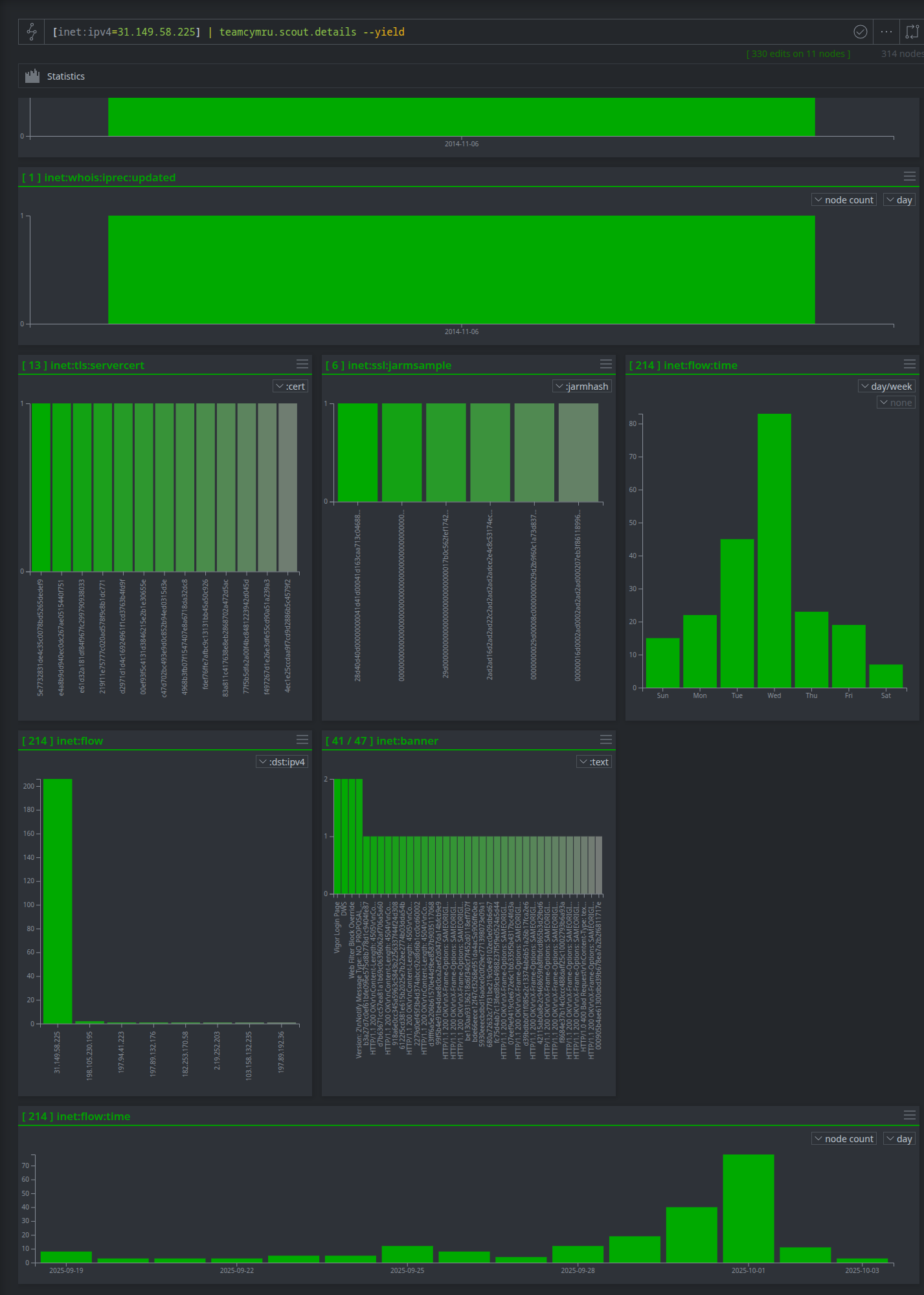
The Power-Up for Team Cymru also allows analysts to carry out deep dives into targeted IP addresses. By carrying out a simple IP query, analysts can discover a deep, multi-faceted threat profile, turning a single indicator into a rich source of actionable intelligence.
- Sample query intent: Investigate the IP address 31[.]149[.]58[.]225 to uncover all associated tags, services, and suspicious certificate activity.
- Scout Query:
31.149.58.225
- Why It's Useful: Synapse’s result panel highlights comprehensive details about this IP from Team Cymru’s data, highlighting several critical insights for an analyst about this malicious IP:
- High-Confidence Tags: The IP is immediately flagged with multiple tags like orb, vpn, and the subtag bravo, confirming it's part of a known malicious proxy network used by APT groups.
- Suspicious Certificates: The platform automatically flags multiple X.509 certificates with recently created dates (e.g., CN=www[.]voj2knr7tqex[.]net created on 2025-09-24) and uncommon certificate durations (e.g., 12 days, 395 days), which are strong indicators of attacker infrastructure.
- Correlated Risk: The platform shows the IP is a VPN, an ORB node, and a host for suspicious domains simultaneously. This holistic view allows an analyst to understand the full context of the threat and respond with confidence.
How to Power-Up Your Queries
While the above queries are powerful, they are only a sample of what this integration with The Vertex Project brings. Please refer to Team Cymru’s Scout API documentation for additional guidance on how to best leverage Scout and make use of the Pure Signal™ data ocean, the largest source of context-rich telemetry data from beyond the network edge.
.png)
.png)
.png)
.png)