Operationalize Pure Signal™ in OpenCTI
Team Cymru’s integration with Filigran makes information from the Pure Signal™ data ocean accessible to analysts working in OpenCTI. This integration joins Team Cymru’s global visibility and context-rich telemetry data with the unified data model of the OpenCTI platform, allowing for frictionless analytical capabilities and a proactive approach to threat hunting and incident response.
By ingesting Team Cymru’s data into OpenCTI via dedicated enrichment and search connectors, analysts can carry out powerful queries of Pure Signal™ data without ever having to leave their threat intelligence platform (TIP). This allows for efficient, confident decisions with a seamless analytic experience.
OpenCTI and Team Cymru’s Pure Signal Promise Deep Enrichment for Incident Response
The integration allows analysts to carry out deep dives into targeted observables. By triggering the Scout Enrichment Connector on a single IP address, analysts can discover a deep, multi-faceted threat profile, turning a simple observable into a rich source of context.
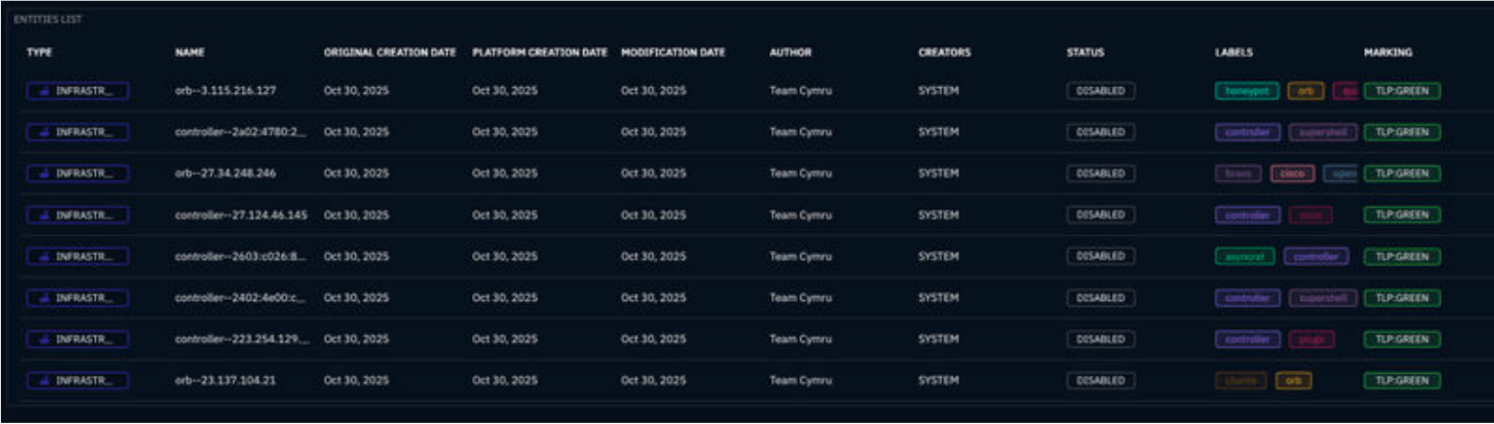
Why It's Useful: OpenCTI’s observable view is immediately populated with comprehensive details from Team Cymru’s data, providing critical insights:
- Infrastructure Mapping: Automatically ingest open ports and banner data to reveal exactly what services are running on the host.
- Relationship Graphing: The connector creates STIX relationships between the IP and its ASN, country, and resolving domains.
- Pivotable Indicators: The IP is linked to specific behavioral indicators (e.g., "controller," "honeypot"), allowing the analyst to click through and see other entities sharing those behaviors.
What are the Use Cases for the OpenCTI Integration
The following queries are representative of some of the powerful methods analysts can use to leverage Team Cymru Scout within OpenCTI to proactively hunt for threats.
Proactive Threat Hunting: Tracking Obfuscated Actors
The Scout Search connector allows for detailed investigations focused on specific actor behaviors. For example, this sample query investigates the intersection of specific geolocation data and proxy usage to uncover obfuscated North Korean actors hiding behind commercial VPN services.
SAMPLE QUERY INTENT:
Identify all communications between North Korean IPs (country code KP or known ASNs) and exit nodes for Astrill VPN, a common tool used by DPRK IT workers to mask their location.
SCOUT QUERY:
cc = "KP" asn = "131279" comms.tag2 = "astrill-vpn"
Why It's Useful: State-sponsored actors often use commercial VPNs to blend in with legitimate traffic. This query cuts through the noise by correlating network origin with behavioral tags. By automating this search in OpenCTI, analysts can convert these results into dynamic, auto-updating lists of "Controller" or "Proxy" indicators.
Infrastructure Analysis: Identifying Commercial Tool Abuse
In OpenCTI, analysts can use Scout queries to hunt for the misuse of legitimate remote desktop tools, which are frequently used for command and control (C2). This query correlates network location with specific Pure Signal™ tags to find anomalies.
SAMPLE QUERY INTENT:
Uncover potential C2 channels by searching for IPs on Russian ASNs (like TTK) that are tagged as AnyDesk nodes.
SCOUT QUERY:
tag = "anydesk" asn = "20485"
Why It's Useful: This query returns IPs using legitimate software for potentially malicious purposes within high-risk networks. Security teams can use this form of infrastructure analysis to proactively hunt for "living off the land" techniques before they are deployed against the enterprise.
Hardware Fingerprinting & Supply Chain Risk
The integration also allows analysts to hunt for physical hardware threats. This query uncovers specific remote access devices, such as PiKVMs, operating within critical ASNs.
SAMPLE QUERY INTENT:
Find IPs tagged as PiKVM devices that are communicating with known North Korean ASNs (Star-KP, TTK, Cenbong).
SCOUT QUERY:
asn = "131279, 20485, 134544" comms.tag2 = "pikvm"
Why It's Useful: Hardware-based backdoors often evade standard software scanning. This query allows for high-confidence threat hunting by fingerprinting the device type and its network neighborhood. Identifying a PiKVM in a sensitive network segment provides immediate, actionable intelligence.
Using OpenCTI for Trend Analysis and Automated Dashboards
By leveraging OpenCTI Playbooks, teams can schedule these hunts to run daily, feeding dashboards that visualize threat velocity and infrastructure changes over time.

Visualize Ransomware TTPs: Build dashboards that track the volume of IPs associated with tools like "Cobalt Strike" alongside ransomware families like "Rhysida" and "BianLian," giving leaders a clear view of the threat landscape.
Comprehensive Malware Family Tracking: Spot spikes in specific threats, such as infostealers or loaders, based on the volume of infrastructure identified by Scout queries.
Ready to Accelerate Your Investigations with OpenCTI and Team Cyrmu?
Combine the power of OpenCTI with Team Cymru's unrivaled Pure Signal™ data. Operationalize your threat intelligence today.
Go to team-cymru.com/opencti to learn more about our integration with OpenCTI, or Request a Demo.
Please refer to the team-cymru/opencti-connectors repository for installation guides.

.png)
.png)
.png)