Analysing Carding Infrastructure
Between July and December 2025, Team Cymru analyzed carding infrastructure using technical fingerprinting, a vital strategy for organizations—particularly financial institutions, law enforcement, and fraud fusion centers—for proactively countering these fraud campaigns.
Team Cymru’s infrastructure tracking capability assists the global defender community to identify carding-related IP addresses before they are fully protected. By using internet-wide scanning, cybercrime intelligence analysts can identify servers as they are created or modified and before they are hidden.
IP addresses identified this way can provide critical evidence for subpoenas, takedowns, and evidence gathering. Further, using Team Cymru’s NetFlow analysis capabilities, researchers can link related infrastructure directly tied to the IP addresses used for carding.
Summary of Findings
- Team Cymru identified 28 unique IP addresses and 85 domains hosting carding markets or carding forums.
- These IPs were hosting the Login Pages or Forum Landing Pages of these sites.
- Many of the ASNs hosting carding infrastructure were offshore infrastructure providers.
- The most common top level domains (TLDs) used by carding infrastructure are .su, .cc, and .ru.
Note: A Scout query has been shared for Team Cymru customers to track the carding infrastructure uncovered.
Background on Carding
To understand how carding works, it is helpful to view it as a sophisticated, multi-stage "supply chain" where criminals specialize in either stealing data, selling it, or converting it into cash, a process known as cashing out. Once data is stolen, it is rarely used immediately by the thief. Instead, it is sold on specialized markets and cybercrime forums. Prices of stolen cards can range from $5 to $150 per stolen card, depending on the card's credit limit, how recently it was stolen, the country of origin, and whether it includes full identity details, also known as fullz.
Credit card data can be harvested at almost every point of a transaction. Magecart groups execute web skimming by injecting malicious JavaScript into compromised e-commerce checkout pages to capture details, while phishing campaigns use deceptive emails and websites to trick users out of their card data.
On a larger scale, database breaches are conducted by targeting the central servers of retail, hospitality, or financial organizations where millions of card records are stored. In the physical world, criminals can deploy skimming devices and hidden cameras at ATMs, gas pumps, and Point of Sale (POS) terminals to read magnetic stripes and record PINs, providing the "dumps" necessary to create cloned physical cards.
Details about how cybercriminals use stolen cards are available in Stripe’s FT3 framework definition. Stripe’s analysts have identified that these stolen credit card details can be used to perform unauthorized transactions on payment platforms like Stripe. Cybercriminals use them to make unauthorized purchases on e-commerce sites that process payments via Stripe or donate to fake charity campaigns processed through Stripe.
Research Methodology
To track carding infrastructure, we utilized a research methodology centered around Team Cymru’s large-scale internet telemetry and metadata analysis, specifically leveraging internet-wide port scanning, passive DNS collection, as well as NetFlow data. This process involves performing Regular Expression (Regex) searches across HTTP and HTTPS title banners on ports 80 and 443 to identify servers broadcasting carding-specific keywords such as "CVV," "Dumps," "Carding," and "Shop." This analysis is further refined by indexing X509 certificates and analyzing Subject Common Names, which allows for the clustering of related infrastructure based on reused certificate attributes.
The advantage of this internet-wide scanning is the ability to identify the underlying origin servers before they are obscured by Content Delivery Networks (CDNs) like Cloudflare. By capturing the server’s identity and host IP address during the initial configuration phase, we can look past CDN-based obfuscation and map the bulletproof hosting environments where these illicit marketplaces and forums reside.
Note: It is worth noting, however, that cybercriminals are known to utilize website cloning techniques to replicate the appearance and attributes of popular carding markets and forums. They do this to phish the credentials from other threat actors and novice users for their own nefarious purposes. Therefore, not every IP address we identified is confirmed to be an operational carding market or carding forum via this method of research.
Carding Markets Versus Carding Forums
While the terms are often used interchangeably in technical research, the sources highlight distinct functional and structural differences between a carding market and a carding forum.
A carding market is primarily a transactional platform and is essentially an e-commerce site for stolen financial data. These are often referred to in the sources as "shops" or "stores" in the cybercrime underground, as well as automated vending carts (AVCs). Dedicated carding markets are typically searchable databases where they can filter stolen cards by country, bank, or card type.
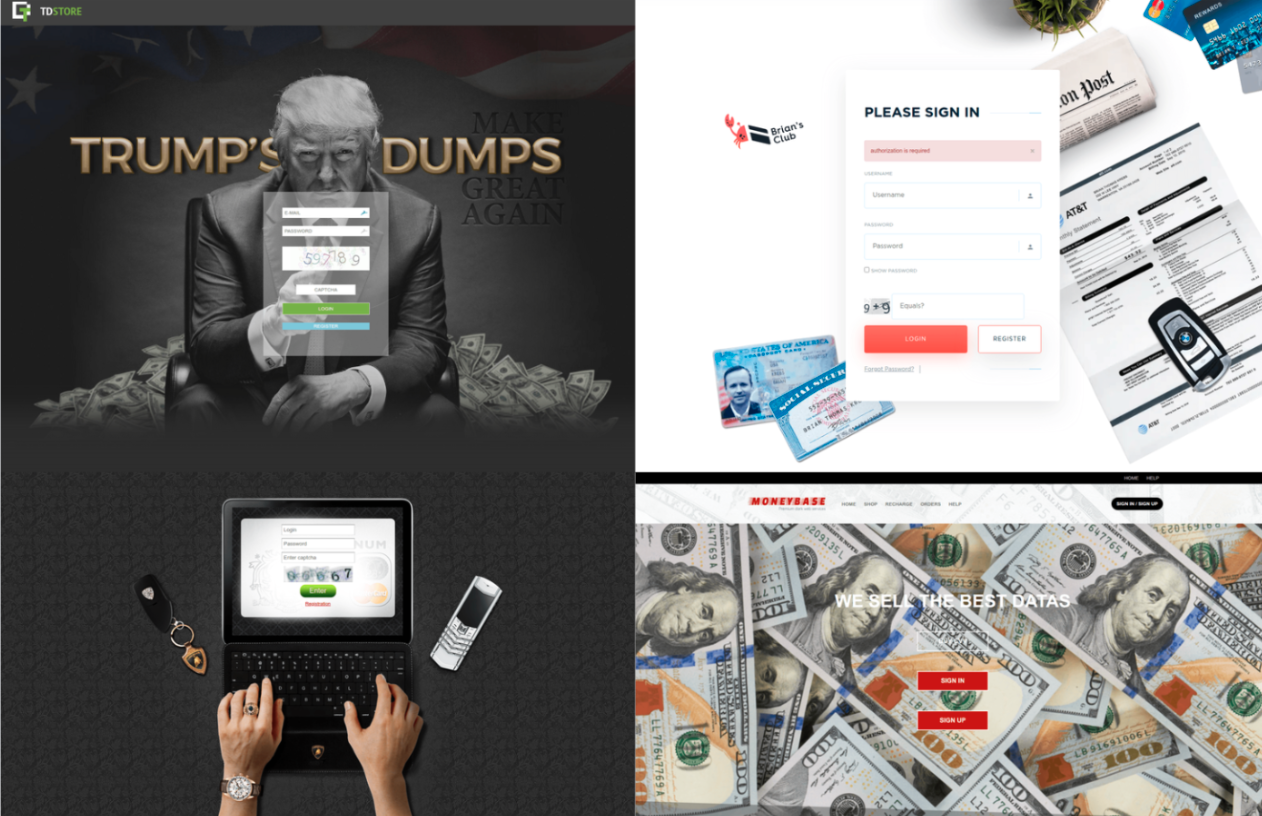
A carding forum is a discussion-based hub where threat actors share intelligence, trade techniques, and build reputations. These platforms facilitate social chatter and networking. They are used for advertising services like Bulletproof Hosting (BPH), sharing feedback on the quality of specific carding shops, and discussing malware or phishing tactics.
Profiling Hosting Providers Preferred by Carders
Team Cymru analyzed the distribution of ASNs from the 28 unique IP addresses discovered hosting carding infrastructure between July and December 2025 in this research.
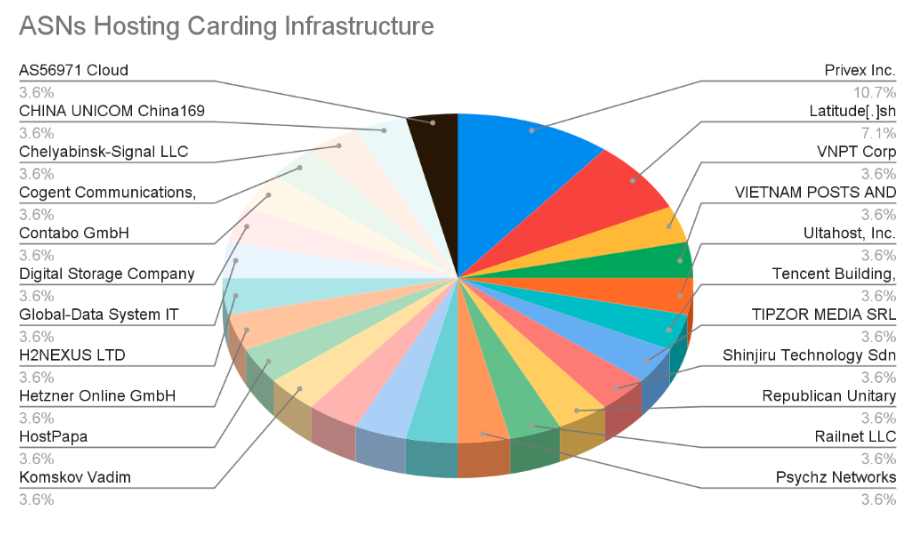
Many of the ASNs hosting carding infrastructure operate in jurisdictions referred to as "offshore," where legal cooperation with international law enforcement may be limited and monitoring the activities of their customers on their infrastructure is also lacking.
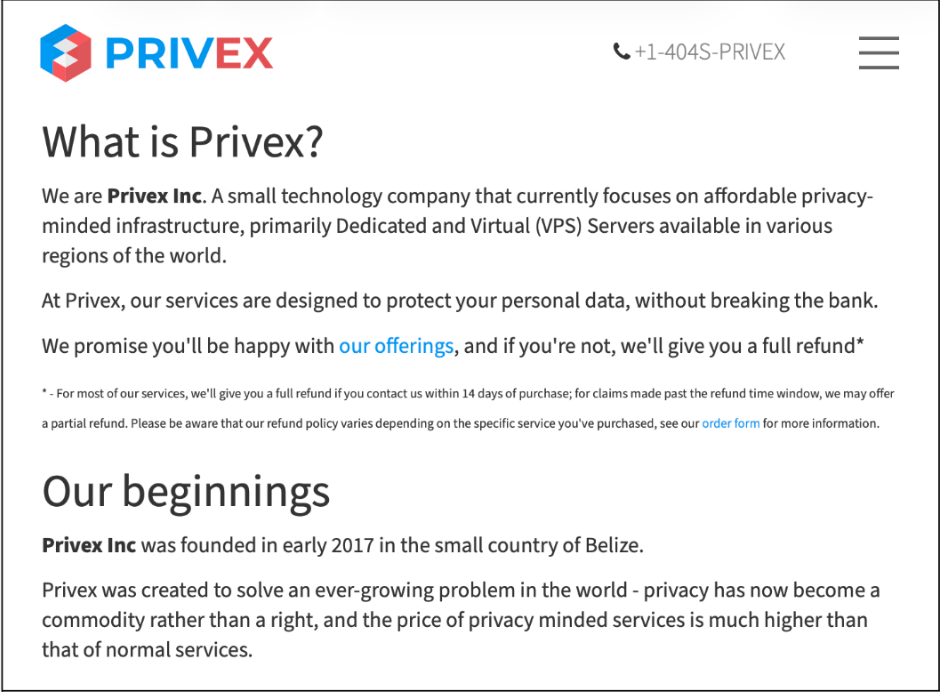
Multiple carding markets were identified that were hosted on Privex servers. This is likely due to Privex advertising their services as “privacy-minded infrastructure” offering dedicated VPS. Criminals can purchase these servers without providing any information about themselves and host illicit content without facing repercussions.
Hosting services preferred by carders are rarely used for a single purpose; they typically host a wide variety of active malware and hacking campaigns. For example, the ASN with the most IP addresses associated with carding markets identified in this research was Privex. Open source reports have observed offensive security tools (OSTs) such as Sliver hosted recently on Privex AS210083.
Top Level Domain Analysis of Carding Infrastructure
Across the 28 unique IP addresses, Team Cymru also identified 85 unique carding-related domains hosted on them. Analyzing the distribution of top level domains (TLDs) revealed some interesting insights, including heavy concentration of the use of .su, .cc, and .ru.
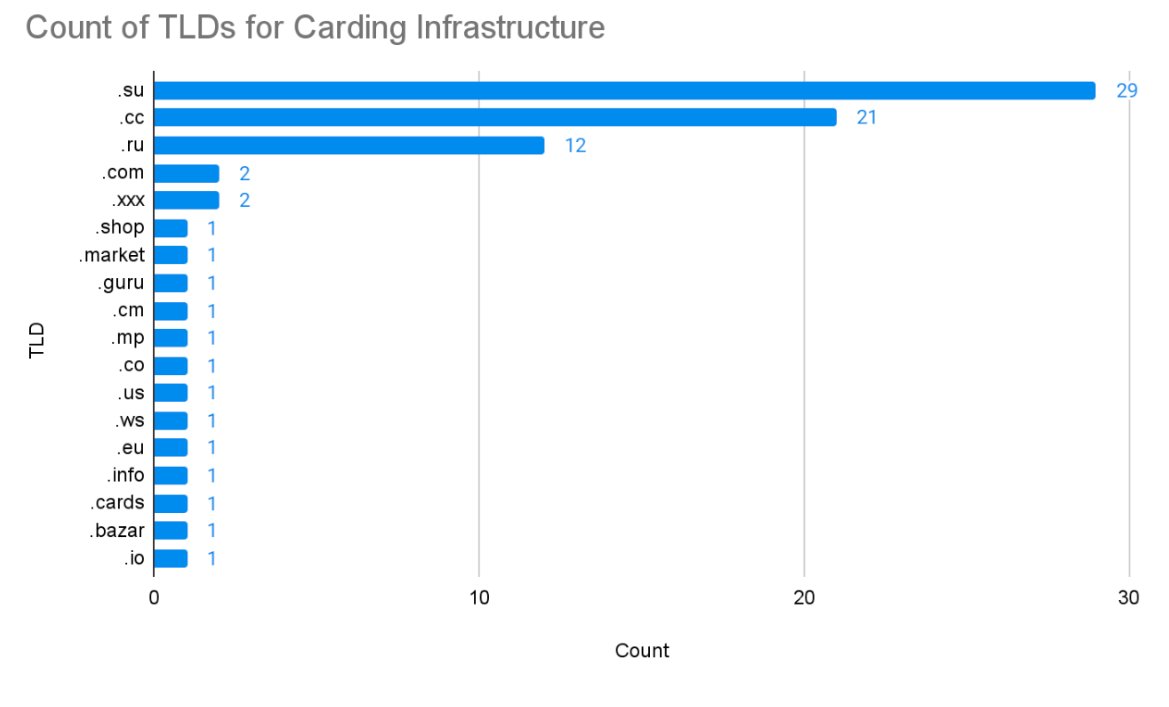
These domains offer a combination of jurisdictional shielding and lack of strict oversight.
- The Soviet Union .su TLD belongs to a country that no longer exists. Its management, therefore, is often considered legacy and has historically had very loose registration and abuse policies.
- Many carding shops likely use .cc because it can stand for “credit card” and is also cheap, easy to register in bulk.
- Sites on .ru can be considered effectively unreachable by Western court orders as long as the server is physically located within Russia.
Conclusion
In conclusion, the fight against the underground economy relies on a deep understanding of its technical foundations. Team Cymru researchers are continuously investigating cybercrime infrastructure using internet telemetry collection capabilities. By leveraging Team Cymru Scout, customers can run sophisticated search queries to proactively identify carding markets and their hidden backend servers.
Through the use of NetFlow analysis, linked infrastructure can be uncovered, allowing fraud teams to bridge the gap between individual fraudulent transactions and the broader criminal networks where stolen data originates. This methodology transforms network intelligence into a proactive tool for disrupting criminal operations and raising the costs for threat actors worldwide.
Customers can use the following Scout query to search for carding infrastructure:
openports.banner.hash = "7ae9e4fa48d05f7850f147e2c371fcac47b70889, f1e3c64bfdf7f38837f891a4583543cdef305080, 306fb5c433fb6d8a3cfb2682a6c97c5caefece13, f72326d36842da941efb3b07450833b86d3eab0d, 4ddb778eb8cae951c674cdca38c1951078743009, 519d8dcc491c794f6d6b3c7aaca4cf5c0dbf1319, d288cc42b2eec356e4eaef941b4987641d6456ac, 2814dfe95d0db67dded7993656e5c348be0b698e, 880ba96eb15fd0dbe56f7e6cf777ce8afd665567, c4ce8db9c180f2a4e7261e477439b96f458691d4, deccc5aa3fc147adadaa4b34a93c76bcbe2574f2, fd1ec39e084966961b23fff7ae12fecd95f05ea6, 5c180d7ee7049d85e567cd6400c62e0ce6629306, 52b51f30a61d66a00e825a6a351d521d910429cd, 75e35902080e3030b88e4fc8f0c8023deaeed97a, bb6a55ae8aa6ad73f1e5c70c5b533a15562ed454, d7a32dee1077ae97481009512a903c5e41c5306b, 546c3d522c939a1f6ff38300eb82c0111130d1c7, 661a5c6a1638b83c25f49cda99f2f809043d83bd, ccdf2f73e80b0d45b089789b82901c8a81120194, fe41569db860e4dc9808b7b2097a8b7e8bac436b, 222d7ce22a5623c52ddb34edfa89d5fafb58bc3a, 557a61eaf0a978e0546ad66a7308aab09465156e, 414d89c6165c9321f073e1872525c2c9dd11f56d, d3501d9dbf31b4611ee56594840f9d02bd81b18f"
Note: Law enforcement agencies who would like the complete list of IP addresses and domains of the carding infrastructure analyzed in this blog can receive them after contacting Team Cymru via our email outreach@cymru.com.

.png)
.png)
.png)