Supercharge Threat Hunting: Team Cymru Pure Signal™ Scout Now Integrated with Google SecOps
For Security Teams: Network Intelligence Meets Cloud-Scale Analytics
Security teams face a critical external visibility gap: While endpoint and log data provide a fragment of the story, network flows from internet traffic reveal the full narrative of an attacker's behavior. It helps answer questions like ‘How did they get it, and where from?’, ‘Are they targeting my suppliers?’ and ‘Where will they strike from next?’. Today, Team Cymru bridges this visibility gap with our official integration between Pure Signal™ Scout and Google SecOps. This powerful combination delivers internet-scale netflow intelligence directly into your security operations workflow, transforming raw metadata into context-rich, actionable threat intelligence.
The Fortune 100's Missing Link: Connecting Pure Signal to Google SecOps
The driving force behind our new integration comes directly from the world's leading enterprises. We recognized that many of our Fortune 100 customers have standardized on Google SecOps, creating strong demand for a native Pure Signal Scout integration. To ensure our solution met the rigorous demands of these mature security operations, we collaborated closely with teams we knew had power users. This crucial feedback enabled us to refine our design, ensuring that the integration seamlessly enriches Google’s native UDM (Unified Data Model) to empower analysts within their primary investigation platform.
Why NetFlow is the Investigator's Missing Lens
NetFlow provides the connective tissue for threat actor reconnaissance, attack reconstruction, and breach recovery, revealing critical patterns traditional tools don’t provide, such as:
- Real-time visibility of ransomware victims among the supply chain for pre-emptive defensive actions
- Obfuscated C2 communications within seemingly legitimate traffic that help to confirm breach recovery success
- Data exfiltration patterns that are invisible to endpoint agents that provide focus and prioritize during incident response
- Proactive defenses made possible through mapping multi-tiered threat actor infrastructure for predictive intelligence
Pure Signal Scout enhances internet-wide observations with enriched context from Team Cymru's global threat intelligence. Threat analysts and researchers gain insights from over 300B+ netflow records daily from across the globe, that is enriched with over 2100 tags for actionable intelligence that helps to drive faster decisions.
How Scout Transforms Google SecOps Workflows
Three Key Use Cases (Direct from Our Deployment Guide):
1. Incident Response: Detecting Malicious Activity
- Identify compromised assets communicating with known bad actors using Scout's real-time IP reputation scoring:
- > When Google SecOps flags suspicious DNS queries, Scout immediately verifies if the resolved IPs are connecting to botnets or active C2 infrastructure."
2. Threat Research: Investigating Compromised Hosts
- Reconstruct attack timelines with bidirectional netflow data::
- > After an EDR alert on ransomware execution, Scout reveals the full infection chain—from initial exploit kit download to lateral movement and data exfiltration volumes."*
3. Supply Chain Breach Detection: Identifying Data Exfiltration
- Spot abnormal outbound flows masked as common protocols:
- > Scout revealed a substantial volume of 'SSH' traffic from a database server to a bulletproof hosting provider—missed by perimeter tools due to encryption.
Custom Resources to Accelerate Value: SecOps Playbooks and Blocks to drive automated actions
We've built battle-tested components for immediate deployment:
- Pre-Built Detection Rules: YARA-L rules identifying beaconing, scanning & data theft
- Response Playbooks: Automated workflows for containment and investigation
Enrichment Templates: One-click asset context expansion (IP reputation, geo-location, ASN)
See It In Action: Exclusive Resources
1. Integration Video Demo:
See how Secops uses the Google-certified App and integration to enrich any IP address with a wealth of information to accelerate investigations and incident response.SecOps in this video
2. Technical Webinar:
Guest Jame Brodsky, Google Cloud’s Head of Global Security Architects, talks with Team Cymru about Advanced Threat Hunting on our Webinar, showcasing NetFlow + Chronicle, and includes a real breach investigation walk-through.
Why This Changes Everything for SOC Teams
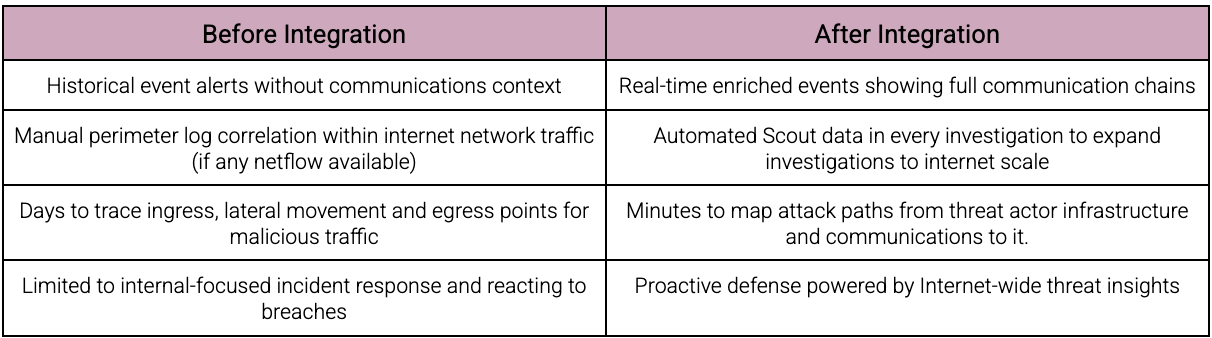
Benefits of Team Cymru & Google SecOps:
- Faster investigation MTTR
- More threats detected through flow-based anomalies
- Proactive hunting with internet-scale telemetry
- Better alignment with business priorities and objectives (PIRs)
Start Seeing the Full Attack with Team Cymru and Google SecOps
Visit the Team Cymru and Google SecOps Webpage:
Watch the Integration Demo
Visit the Team Cymru Github page and download Pre-Built Detection Rules
Request a Scout + Google SecOps Demo
Knowledge is power. Google SecOps with Team Cymru intelligence is both.