Team Cymru Tags Explained: Powering Faster, Smarter Threat Intelligence
Introduction
Security teams are drowning in noisy data. Yet, the difference between catching a threat early and missing it entirely often comes down to one thing: context.
This is where Team Cymru Tags come in. Tags are labels applied to IP addresses to classify behavior, infrastructure, or risk — giving analysts immediate clarity on what they’re looking at and why it matters.
Whether you’re triaging alerts, threat hunting, or tracking a specific adversary, Tags help analysts cut through noise and focus on what’s relevant. This blog breaks down what Tags are, how they’re applied, and why Team Cymru’s tags are a game-changer in modern threat intelligence.
What Are Tags?
Tags like labels in a library. Just as books are classified as “History” or “Science Fiction,” IP addresses on the internet can be labeled as “Bot,” “Cloud,” “Scanner,” or “Phishing.” Each label gives you context — instantly.
These Tags form a taxonomy of threat and infrastructure types that help analysts make sense of the internet at scale.
Team Cymru Tags are accurate because they are created by a mix of machine logic and human analyst review (by our own S2 Threat Research team), applied to observed infrastructure using our unmatched global telemetry.
How Tags Work
Every IP that Team Cymru observes can be tagged with:
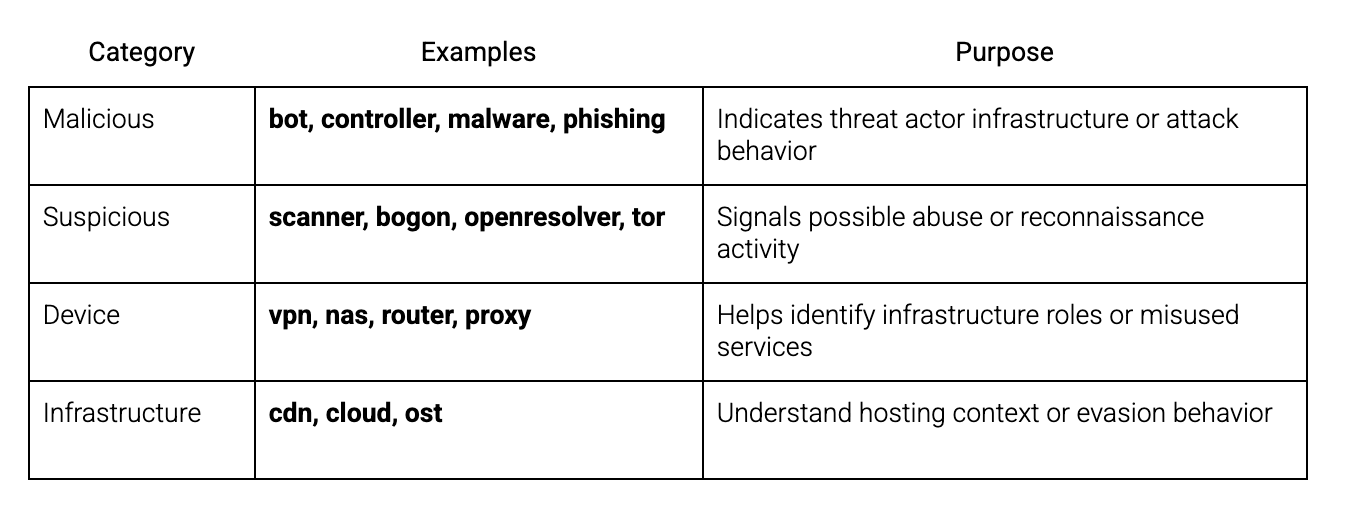
- A Parent Tag (e.g. bot, aws)
- A Child Tag where applicable (e.g. darkcomet, af-south-1, mirai)
This hierarchical structure allows analysts to zoom in from broad behavior types (like malware infrastructure) to specific threat actors or tools.
In our documentation we also provide A Tag Family (e.g. bot, controller, cloud) and A Parent Tag Descriptor (e.g. Bot Family, Cloud Region) to further enhance user understanding.
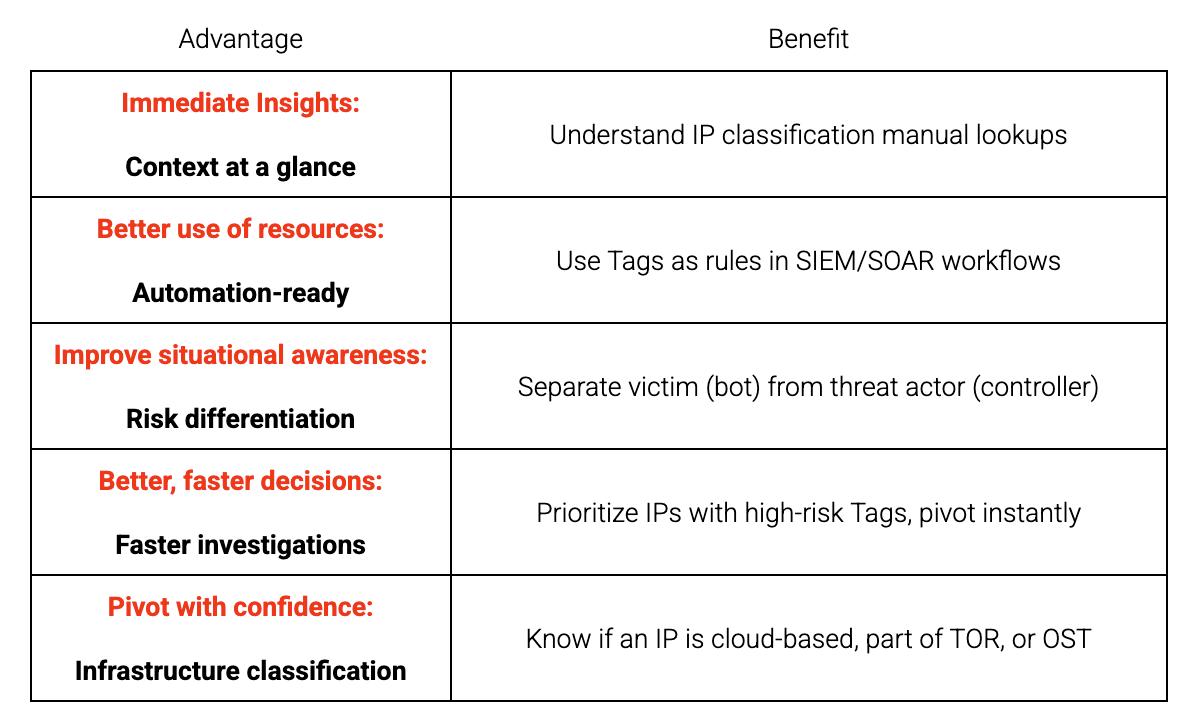
Why Tags Matter: Analyst-Centric Benefits
Immediate Context
Tags give analysts an at-a-glance understanding of what an IP represents. No need to cross-reference five tools — context is already there.
Faster Investigations
With Tags visible in Scout or Recon, analysts can pivot quickly. For example, a controller tag linked to DarkComet tells you this is likely C2 infrastructure for a RAT.
Automation-Ready
Tags can be exported or fed into SIEM/SOAR pipelines, enabling alerting, triage, or blocking based on behavioral categories — not just IP lists.
Enriched Decision-Making
They help prioritize action: controller tags signal active infrastructure, while bot tags indicate victims. That’s a critical distinction during incident response.
Tag Categories and Examples
Using Tags in Scout: For the Frontline Analyst
In Pure Signal™ Scout, Tags appear in:
- Timeline view: See Tags correlated to specific flows over time
- Communications tab: Tags help classify remote endpoints and contextualize behavior
- Filtering and pivoting: Analysts can filter flows using tag logic (e.g., NOT controller, phishing AND cloud, etc.)
Example:
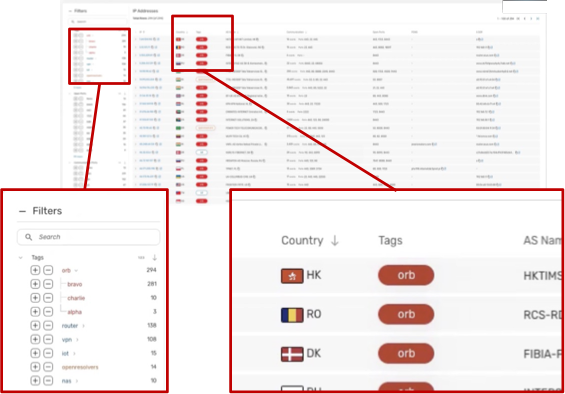
You're investigating outbound connections from a third party to a compromised host. One IP is tagged controller, darkcomet, and cloud — now you know it’s:
- Likely a C2
- Running DarkComet
- Hosted in cloud infrastructure (possibly short-lived)
Without leaving Scout, you now have attribution, intent, and infrastructure context — all from Tags, and the next action is to inform the third party of the compromise with precise information on how to block communications.
Here is a visual example of ORB tags without the Scout UI, where you can also see a Tag Filter panel on the left to help focus results.:
Using Tags in Recon: For Deep Reconnaissance
In Pure Signal™ Recon, Tags can be used to:
- Search historical behavior of IPs over the past 90 days
- Filter or pivot on Tag Families or child Tags (e.g., Tag: controller.family = darkcomet)
- Highlight campaign patterns by isolating infrastructure tagged as malware C2s or phishing
- Identify shared infrastructure used across malware families or threat actor sets
Advanced analyst workflows can rely on Tags to:
- Identify controller clusters using similar hosting or TLS fingerprint patterns
- Correlate bot-infected victims to known C2 endpoints
- Map infrastructure overlap between threat groups (e.g., shared CDNs or proxy services)
Case Study: Tags vs. Malware C2 Panels
Analysts can use Tags to trace back malware families like Warzone, Quasar, or XWorm.
By layering Tags over IPs identified in flow data:
- Analysts can discover repeated connections to endpoints tagged controller.family: warzone
- By filtering out infrastructure on CDNs and shared hosts using NOT tag: shared
- Use Recon to trace the C2 panel’s broader infrastructure, surfacing new IPs with similar behaviors or metadata
This is threat actor profiling — automated and repeatable — using Tags.
Analyst Advantages: Why Tags Matter
Conclusion: Labels that Make Data Actionable
Team Cymru Tags turn billions of flow records into focused, investigable intelligence. By labeling IPs based on what they are and what they do, Tags give defenders a starting point — and a path forward — in the middle of the fog.
For CTI teams, SOC analysts, and threat hunters alike, Tags accelerate investigations, improve precision, and make threat intelligence truly actionable.
Next Steps
Ask our team about Tags as part of our Scout and Recon user experience, and how it can transform your research and investigations
Already a Recon or Scout user? Try a query now with these simple query examples:
- search to identify Neptune servers use tag = "neptune"
- search to identify Gremlin servers use tag = "gremlin"
- search to identify ORB related nodes use tag = "ORB"
.png)
.png)
.png)
.png)