Fingerprinting Malware C2s with Tags
Introduction
This blog is written for threat analysts, defenders, and CTI teams who use our Scout platform—but even if you’re not a user today, it offers practical insight into how advanced research teams fingerprint C2 infrastructure, and how you might apply similar methods using your tools.
Introduction to Fingerprinting and Tags
Fingerprinting Malicious Infrastructure
The art of fingerprinting adversary infrastructure involves identifying the attributes of an IP address and using them to build up a profile specific to the way it is configured. This includes reviewing open ports, banners, x509 certificate(s), TLS handshakes, passive DNS (pDNS), and WHOIS data of the IP address. We then look for unique and common characteristics and either filter out or include them in our queries.
Tags
At Team Cymru, we have developed the ability to query for all the IP addresses that match certain attributes using Tags. These Tags will then appear in the NetFlow records and are searchable within our Pure Signal products, including Scout and Recon. They can be used to filter out or inspect certain network traffic.
For our researchers and our customers, the use of IP attributes and Tags supports the ability to quickly identify communications between malicious command-and-control (C2) IP addresses. Using Scout, we can view how many IP addresses are currently tagged for any type of Tag we track. This can then be used to create statistics over time to track the prevalence of such IPs, thus providing insights into trends and emerging threats.
Some Team Cymru Tags go beyond IP attributes and use NetFlow records for tagging. For example, operational relay box (ORB) networks are notoriously challenging to identify, map, and track due to their dynamic nature being compromised SOHO routers and use of obfuscated traffic paths that bounce from IP to IP. Team Cymru is best positioned to be able to tag IPs as ORBs due to the additional behavioral analysis our researchers can perform, instead of purely relying on IP attributes from other data sources like open ports and X509 certificates that infer an IP could be malicious, it is based on observations that validate it is.
New Tags are regularly created by Team Cymru researchers and are available for all Scout and Recon customers. There are also over 2,100 context Tags available to query in Team Cymru at the time of writing.
In this blog, we were able to fingerprint the malware C2 panels mentioned below and have created new Tags to track their creation as well as their usage and victims in our NetFlow data ocean.
New Tag: Neptune Loader Panels
Neptune Loader was first advertised in November 2023, by a forum member named “M0HX” who made a post on hackerforums[.]net. In the developer's own words, “Neptune is an innovative HTTP loader project that provides robust and efficient control over computer systems through commands administered via user-friendly web panel.” The malware was recently analysed by Cypho, who managed to compromise and investigate a Neptune Loader control panel.

To be able to find a fingerprint for Neptune Loader controllers, we can use the open ports data found in Scout summaries shown below. We can see that port 3000 is open and its HTTP.TITLE is “Neptune - Login” on 25 June 2025. This is an example of a Banner that can be used to create a fingerprint and find any other Neptune Loader controller IPs on the internet in Team Cymru’s open port data, which we then convert into a Tag.
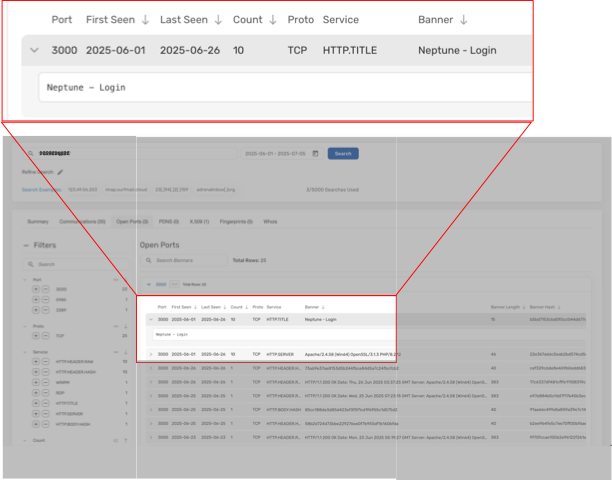
For customers of our Scout product, here is a handy search to identify Neptune servers:
- tag = "neptune"
New Tag: Gremlin Stealer Panels
In April 2025, Palo Alto Networks shared its analysis of a new malware family called Gremlin Stealer, which was being offered for sale via cybercriminal Telegram channels initially. Gremlin Stealer has been spreading in the wild since at least March 2025, according to PAN researchers. Its capabilities include bypassing Chrome cookie V20 protection to steal the following types of data: web browser cookies, stored autofill data, clipboard data, and credentials from applications like FTP clients, Steam, Discord, and Telegram.

To be able to find a fingerprint for Gremlin Stealer controllers, we can use the open ports data found in Scout summaries. We can see that port 80 is open and its HTTP.TITLE is “Gremlin Access” on 27 June 2025. This is an example of a Banner that can be used to create a fingerprint and find any other Gremlin Stealer controller IPs on the internet in Team Cymru’s open port data, which we then can also convert into a new Tag.
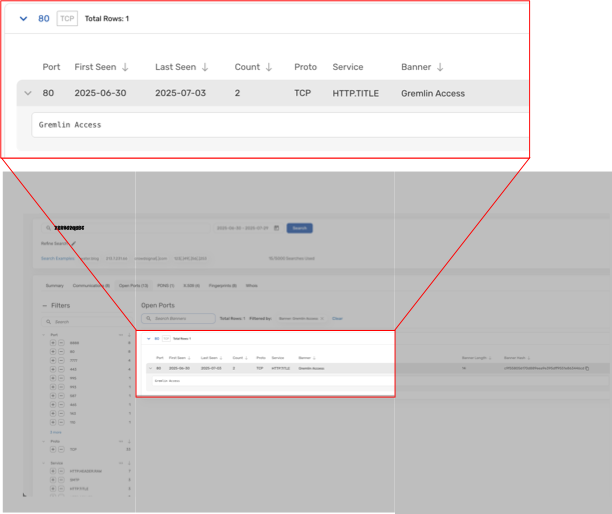
or customers of our Scout product, here a handy search to identify Gremlin servers:
- tag = "gremlin"
New Tag: Unam Web Panels
First released in November 2021, UnamWebPanel by UnamSanctum is a web panel used to monitor and manage SilentCryptoMiner, a publicly available malware, which has been used by cybercriminals to perform unauthorized cryptocurrency mining. The SilentCryptoMiner has been used in multiple campaigns that have been recently disclosed. In March 2025, Kaspersky researchers shared a blog about a campaign spreading the mining malware via YouTube tutorial videos. In October 2024, the researchers also observed SilentCryptoMiner being distributed via search engine optimization (SEO) poisoning (T1608.006) and abused the Wazuh SIEM agent to install it.
To be able to find a fingerprint for Unam Web Panel controllers, we can again use the open ports data found in Scout summaries. We can see that port 80 is open and its HTTP.TITLE is “Unam Web Panel - Login” on 7 July 2025. This is an example of a Banner that can be used to create a fingerprint and find any other Unam controller IPs on the internet in Team Cymru’s open port data, which we then can also convert into a new Tag.
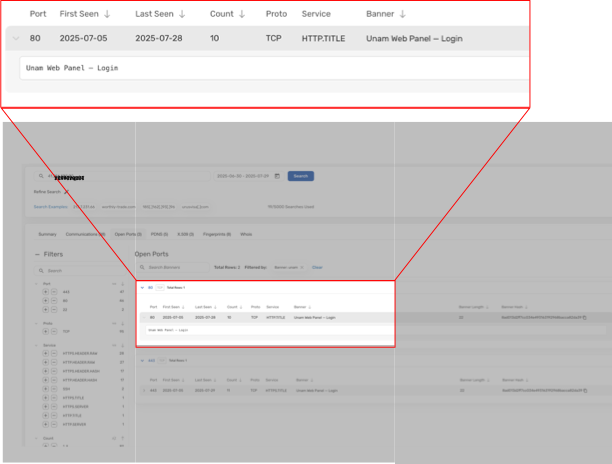
For customers of our Scout product, here a handy search to identify Unam Web Panel servers:
- tag = "unam"
Identifying Targets and Victims
Scout customers can create an advanced query for all of the IP addresses we identify as belonging to the above-mentioned malware families using the following query:
- tag = "neptune, gremlin, unam"
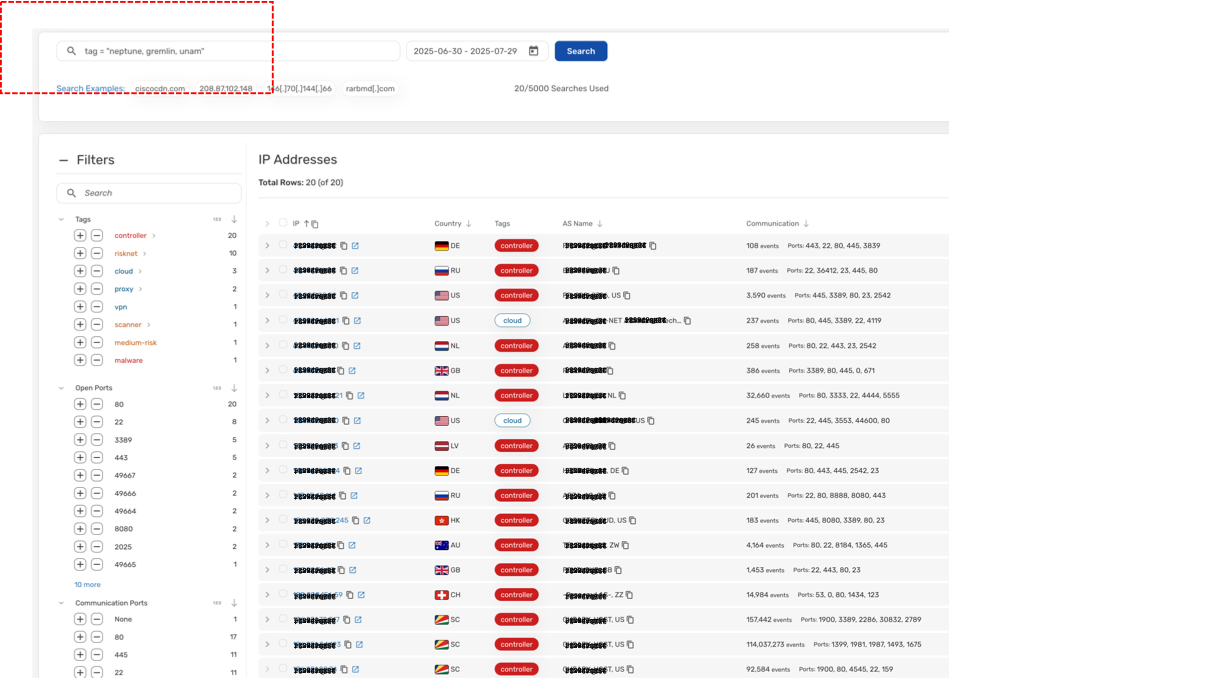
It is then possible to copy all of those resulting IP addresses in Scout as follows:
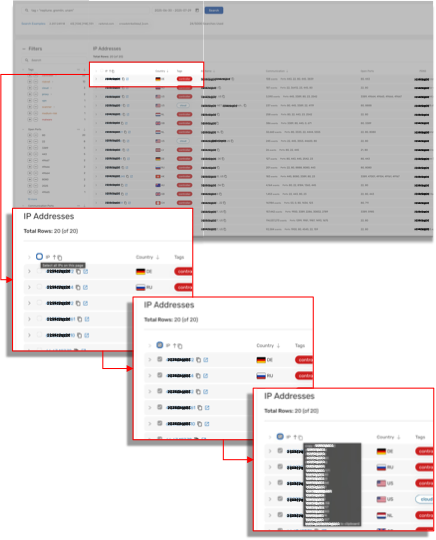
Then, perform a look up for all of the IP addresses that have communicated with them using the following query:
- comms.peer = “<list_of_IP_addresses_separated_by_commas>”
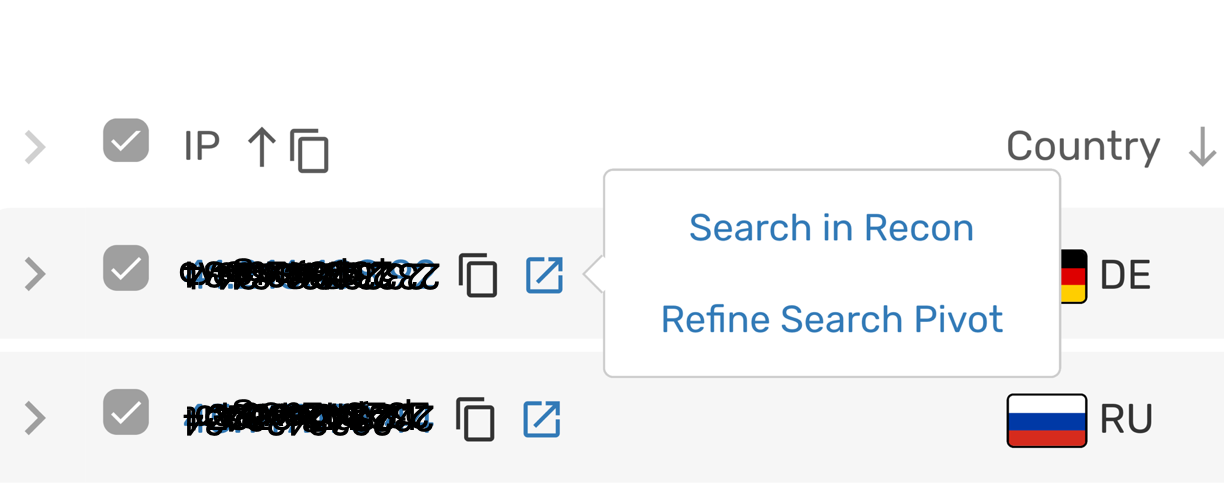
Then, to drill down into the connections between target IP addresses and the controller IPs, Scout customers can click on the “Refine Search Pivot” button to view the exact communications between the target IP and the controller IP.
Example of a summary of sampled NetFlow records in Scout between the potential victim IP (left) and a Neptune Loader controller IP (right):
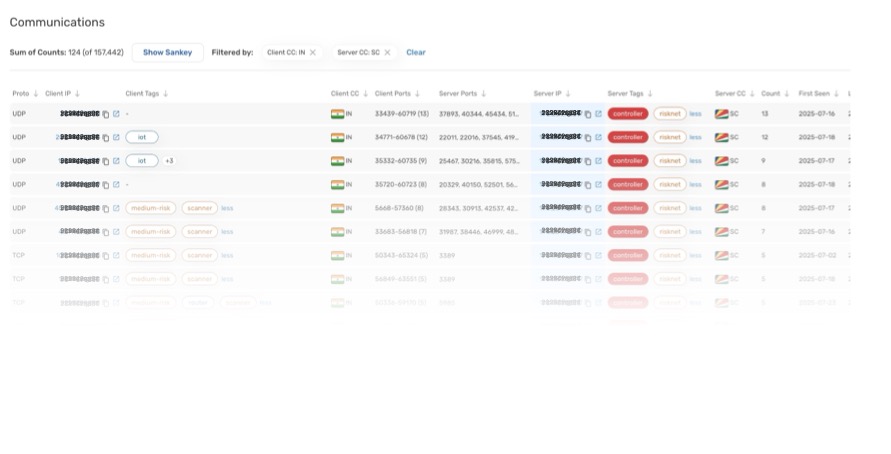
Further, to identify the most likely victim IPs, Scout customers can filter using the “router” Tag and look for enterprise-level devices acting as an internet gateway for the corporate enterprise. The could indicate the malware is present on an endpoint inside the organization’s network and is beaconing back to the controller via the gateway.
Conclusion
Team Cymru researchers are continuously researching adversary infrastructure for emerging threats and developing new Tags as well as enhancing our Tags used to fingerprint live threat actor infrastructure and report them as they appear.
Indicators of Compromise (IOCs)
Neptune Loader
196.251.72.217
196.251.72.216
196.251.72.215
Gremlin Stealer
217.119.129.92
207.244.199.46
Unam Web Panel
62.60.248.110
103.251.164.121
129.151.135.50
196.251.84.193
196.251.90.74
Please note: The IOCs listed above were active at the time of analysis but may no longer be in use. They are provided for historical reference, enrichment, and retroactive threat hunting purposes. Validate before operational use.
.png)
.png)
.png)
.png)